March 6
Plan mode
Start every task with a plan. Plan mode adds a structured planning phase to Ona conversations where the agent gathers requirements through interactive questions, writes a specification, and waits for your approval before writing any code.Select “Plan” from the mode dropdown in the conversation input or from the home screen. Describe your task, and the agent asks clarifying questions as clickable multiple-choice options. Pick a choice, type a custom answer, or skip. Once the agent has enough context, it writes aspec.md with the full implementation plan. Review the spec, then click Build (or press Cmd+Shift+Enter) to start implementation.Available on all plans.What else we’ve shipped
New
New
- Forward environment ports to your local machine with
ona environment port forward. - Ona prompts you to rebuild the dev container when you change a secret, so the new value takes effect immediately.
- PR links and preview URLs now appear as clickable outputs in the conversation.
Improvements
Improvements
- Environments start faster, especially for repositories with many files.
- Conversations with screenshots respond faster.
- A banner in the conversation view suggests converting a repository to a project for faster startups.
Bug fixes
Bug fixes
- Long-running agent tasks no longer disconnect mid-stream.
- The CLI reconnects automatically instead of hanging on a dropped connection.
- Stale action buttons are cleared when they no longer apply.
February 2026
Code review experience
Review code changes and request reviews from Ona directly in the conversation.Leave inline comments — Review Ona’s work by leaving inline comments in the code changes panel, just like reviewing a PR. Highlight the relevant code lines, leave your questions or feedback, and send them off to Ona. Ona will act on the comments accordingly.Request a review from Ona — Ask Ona to review the current code changes before merging. Ona examines the diff, leaves inline comments with suggestions, and flags potential issues — giving you a second pair of eyes without waiting for a teammate.Create a PR directly — Once you’re happy with the changes, create a pull request straight from the conversation. No need to switch to your Git provider — Ona commits, pushes, and opens the PR for you.Organization skills
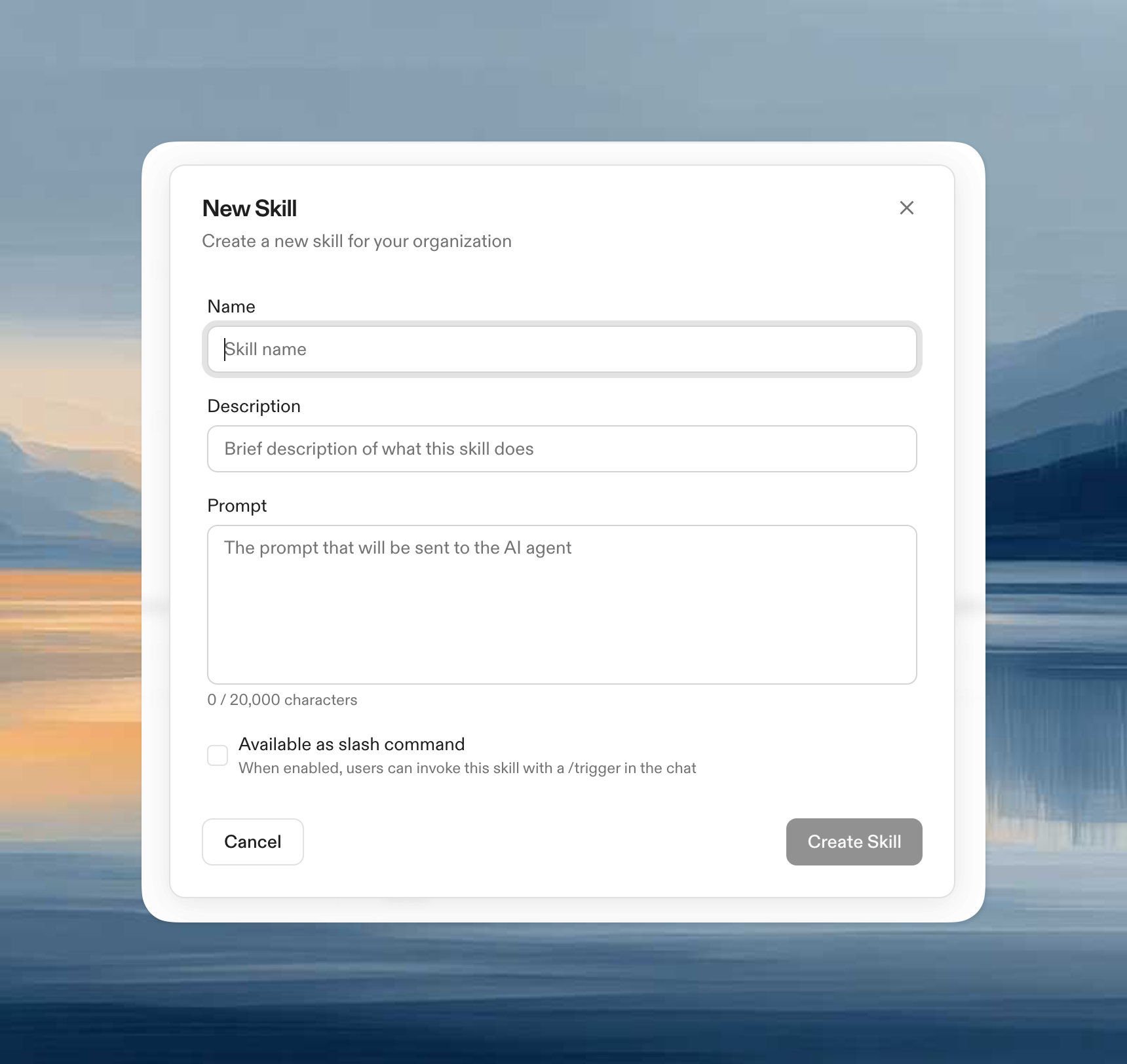
Agent Skills now work at the organization level. Create reusable skills that Ona Agent discovers and uses proactively across every conversation in your organization. Skills capture your team’s best practices (code review checklists, test strategies, deployment procedures) and share them with everyone.What you can do:- Create and edit skills with a name, description, and prompt. The description tells the agent when to apply the skill automatically.
- Optional slash commands. Toggle a
/triggerso users can also invoke a skill manually in the chat. - Import defaults. Start with a curated set of skills (Pull Request, Documentation, Explain Code, Catch Up) and customize from there.
- Search and filter. Find skills by name, description, or trigger.
- Migrate legacy commands. Existing slash commands can be migrated to skills with one click, preserving their trigger while enabling proactive discovery.
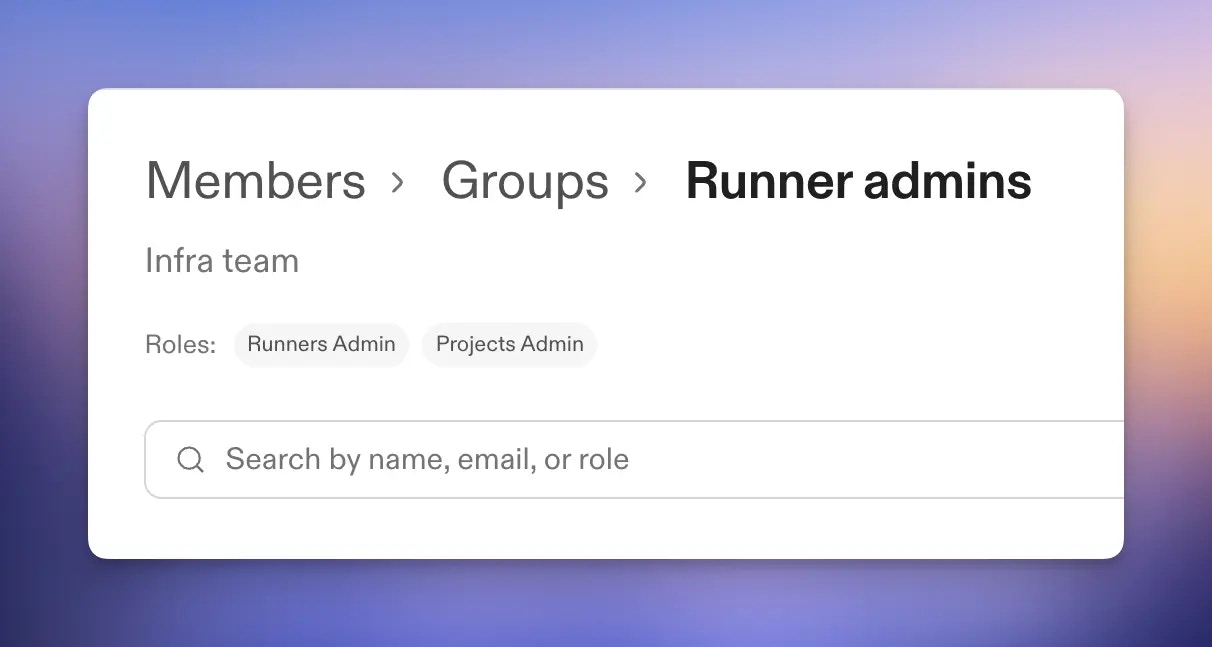
Organization roles for groups
Delegate administrative responsibilities in your Enterprise organization without granting full admin access. Assign organization roles to groups so team members can manage specific resource types across the organization.Available roles:| Role | Grants admin access to |
|---|---|
| Runners Admin | All runners |
| Projects Admin | All projects |
| Groups Admin | All groups |
| Automations Admin | All automations |
Automations
Automations execute multi-step workflows across your repositories — from routine maintenance to large-scale refactoring. Define steps, choose a trigger, and let them run in isolated environments with your tools, dependencies, and guardrails.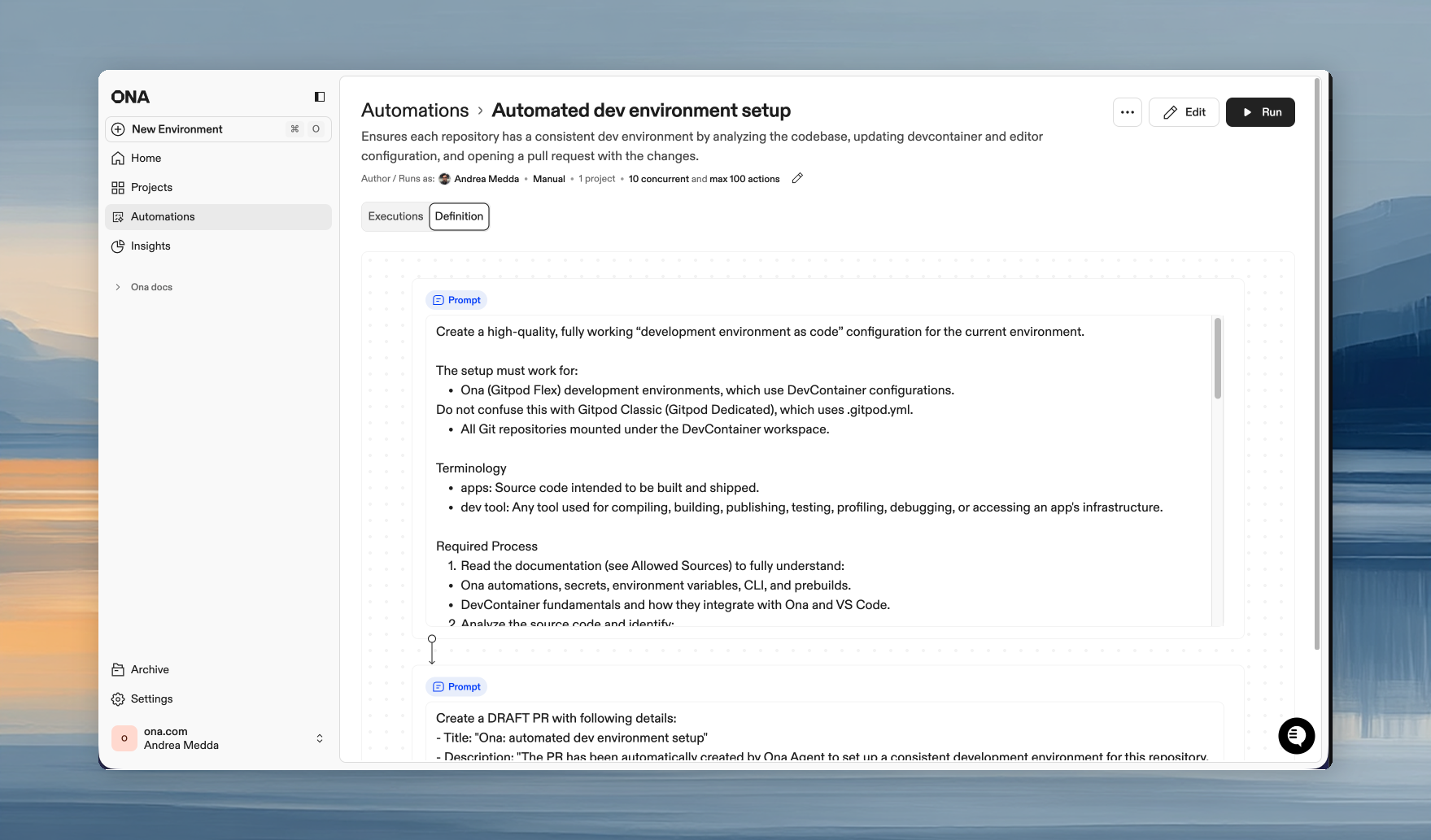
- Define — Combine steps in sequence: prompts (agent-driven tasks), shell scripts, pull request creation, and report extraction
- Trigger — Run manually, on pull request events via webhooks, or on a time-based schedule
- Execute — Run across repositories in parallel, each action in its own isolated environment
- Review — Monitor progress in real time, inspect logs, and approve PRs before merging
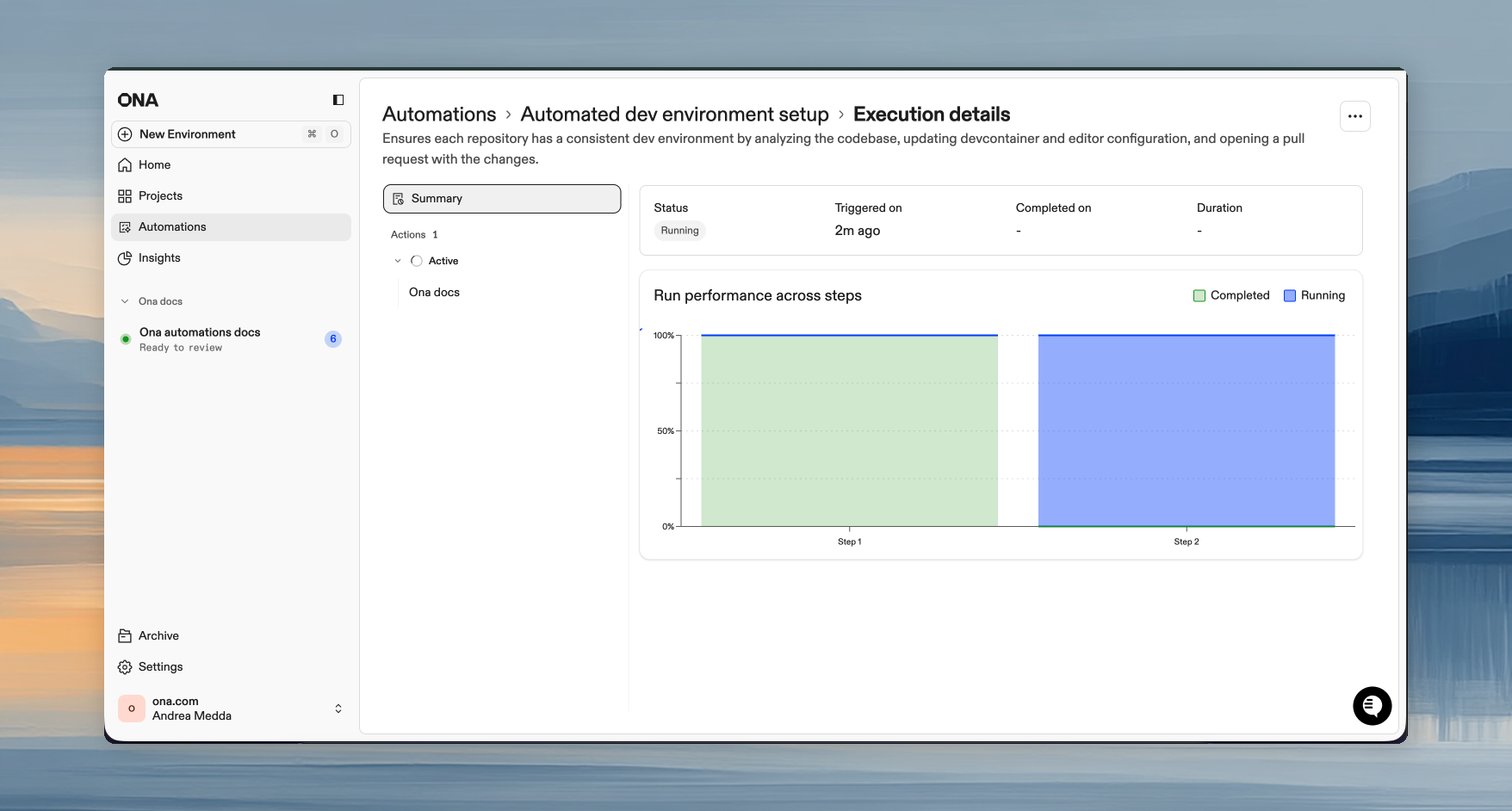
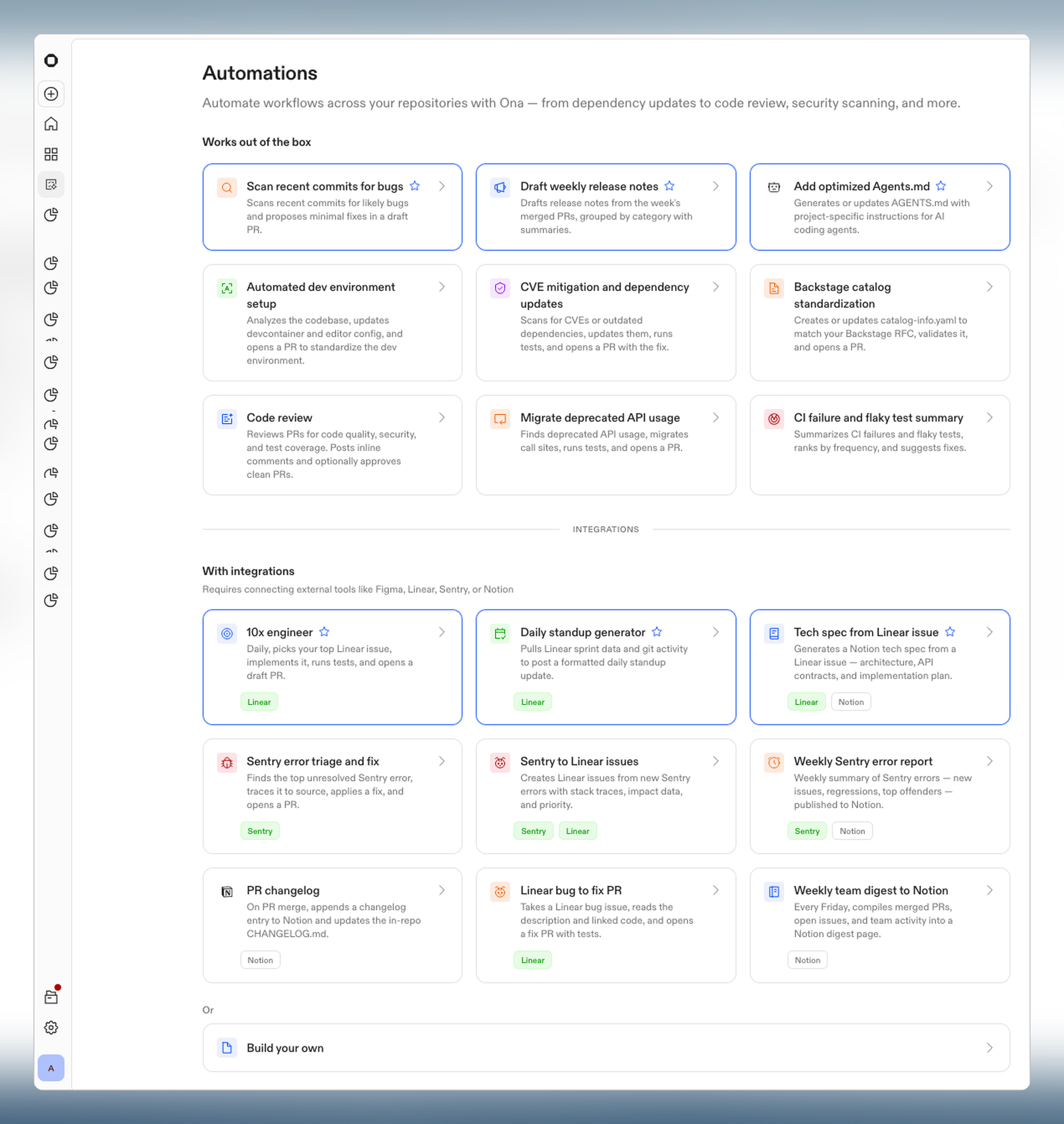
| Role | Permissions |
|---|---|
| Admin | Edit, delete, share, run, view all executions |
| Executor | Run and view own executions |
| Viewer | Read-only access |
SCIM provisioning (beta)
Ona now supports SCIM (System for Cross-domain Identity Management), letting your identity provider automatically create, update, and deactivate user accounts. Link SCIM to an existing SSO provider, and directory changes in your IdP are reflected in your Ona organization without manual intervention.Currently supported identity providers:- Microsoft Entra ID
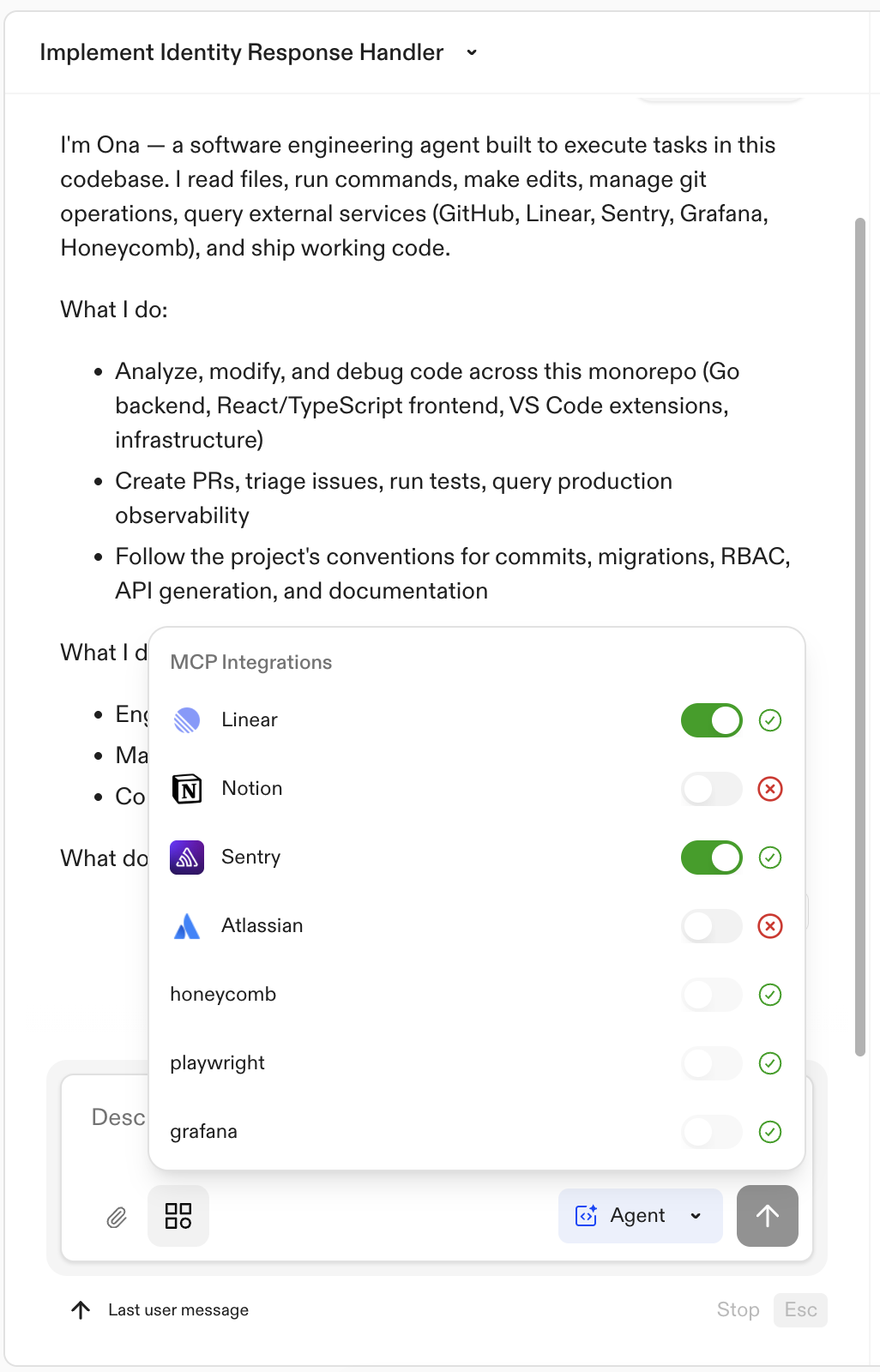
New MCP integrations: Atlassian, Notion, and Sentry
Ona Agent now supports three new MCP integrations — Atlassian, Notion, and Sentry. Once enabled by an organization admin and authenticated by individual users, agents can interact with these services directly from conversations.- Atlassian — Manage Jira issues, search Confluence, and link code changes to tickets. Configure Atlassian
- Notion — Search pages, read documentation, and access project wikis. Configure Notion
- Sentry — View errors, analyze stack traces, and track regressions. Configure Sentry
Secrets available during Dev Container builds
Organization and project secrets may now be used during Dev Container image builds via secret mounts — without baking them into the final image.EachRUN step in your Dockerfile must explicitly request the secrets it needs:Ona now runs on Claude Opus 4.6
We’ve upgraded Ona to Claude Opus 4.6, Anthropic’s latest flagship model. At the same price as Opus 4.5, you’ll see significantly better results across a range of tasks, especially for complex problems.
- Adaptive thinking - The model decides when to think deeper, no manual tuning needed.
- More output tokens: Twice the previous limit, better for large refactors and file generation.
- Improved tool use: More accurate code edits and fewer mistakes.
AWS eu-south-2 region now supported
You can now install a Runner in AWS regioneu-south-2 (Spain). When you do, a default environment class is created: Extra Large (Spot). From there, you must configure additional environment classes as custom classes.For eu-south-2, we recommend using instance types from the m7i (compute) and g6 (GPU) families.Getting started:Automatic credit top-ups
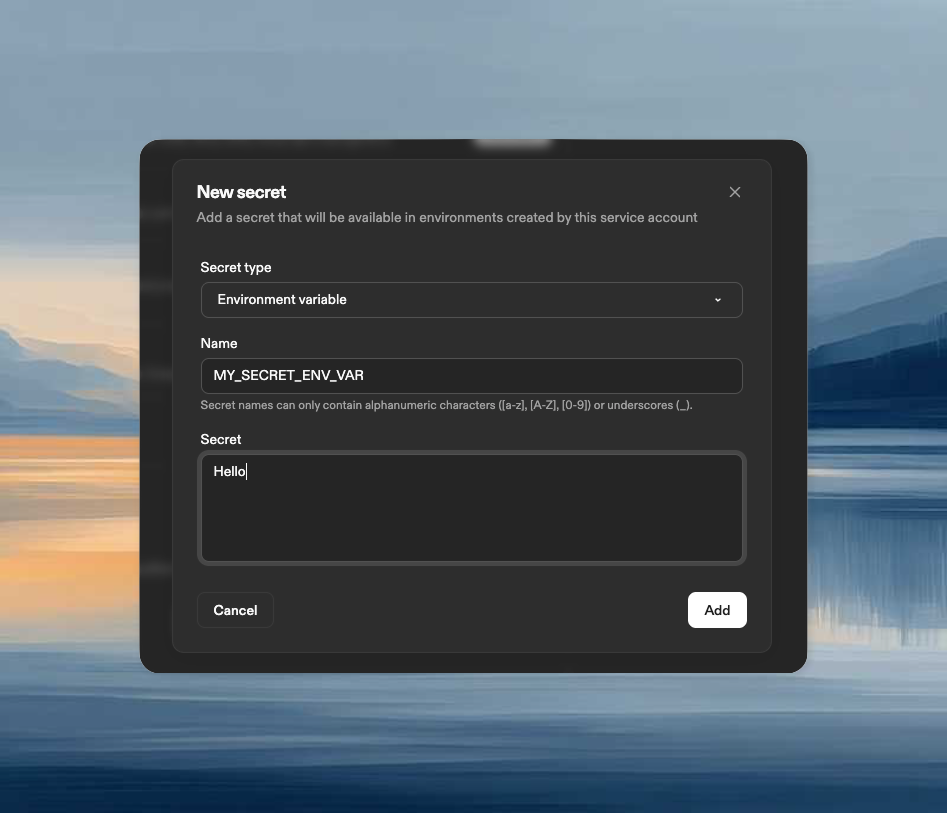
Core plan organizations can now enable automatic credit top-ups. When your credit balance runs low, Ona automatically purchases additional credits using your default payment method.Enable auto top-up and choose a top-up amount at Settings → Billing.Learn more about auto top-upService account tokens and secrets
Service accounts now support tokens and secrets, enabling programmatic API access and secure credential management for automations.Tokens — Organization admins can issue long-lived tokens (up to 90 days) on behalf of service accounts. Use these for CI/CD pipelines and external scripts that need to start automations or query the API.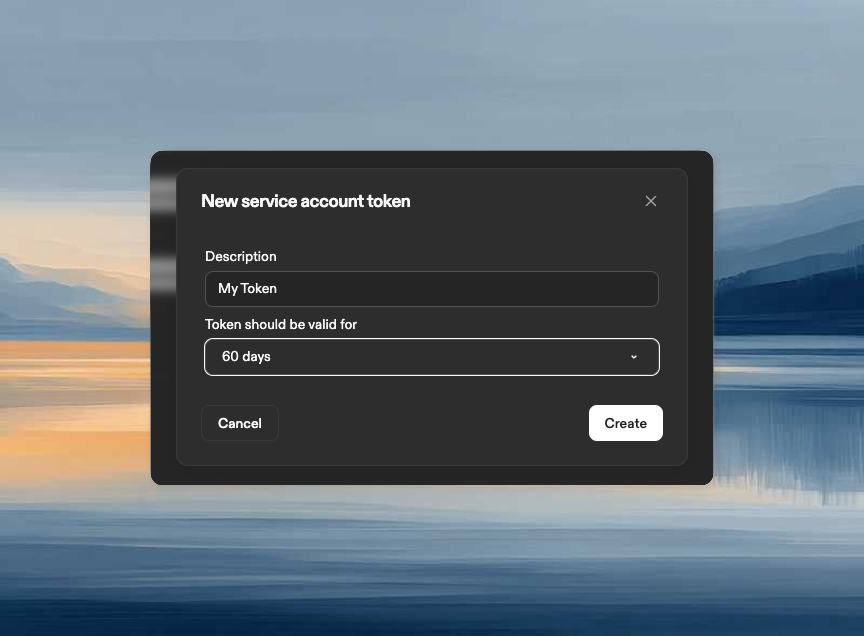
January 2026
Share resources with individual users
Sharing a project with a colleague no longer requires creating a group or asking an org admin. Resource admins can now share directly with individual users.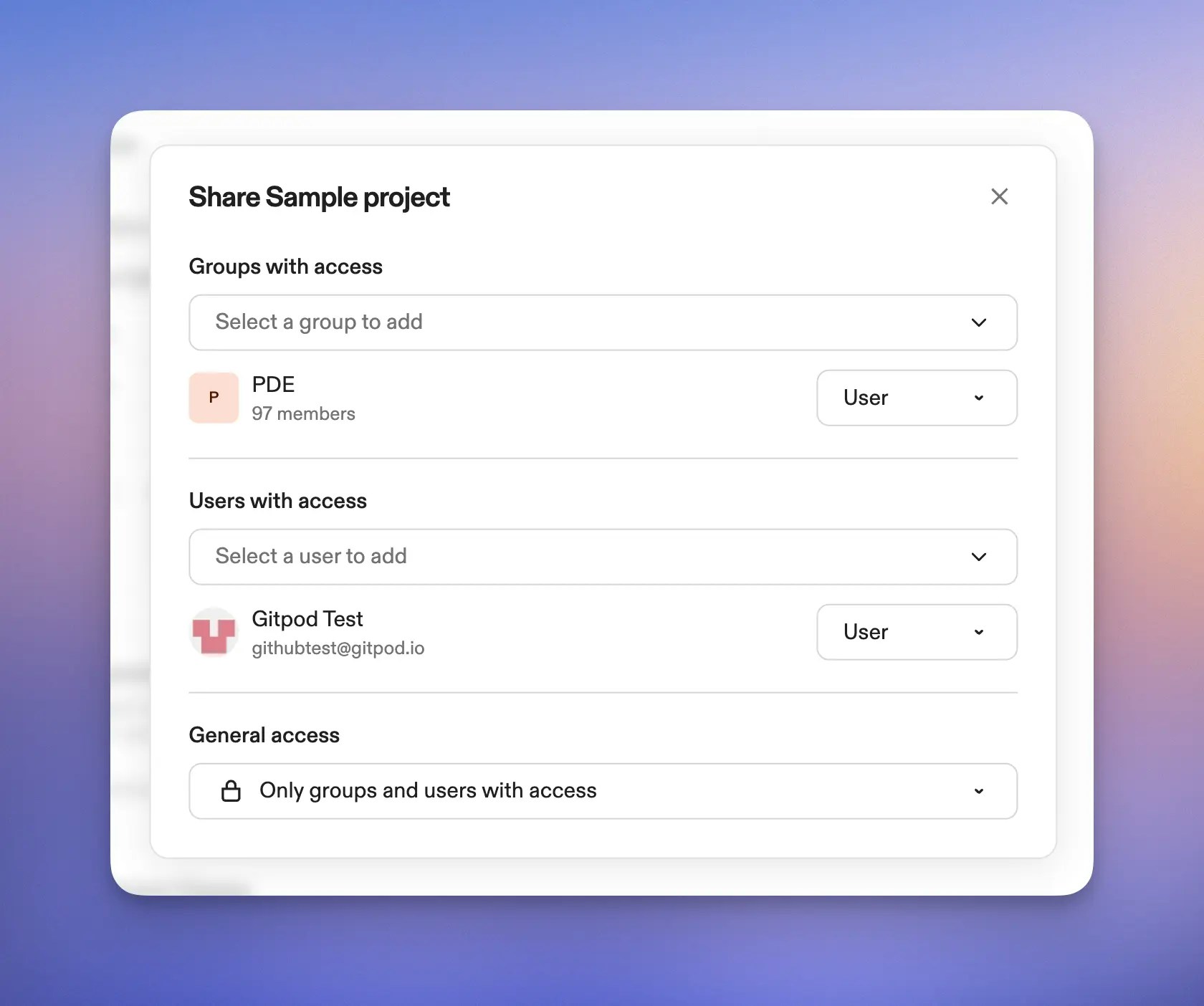
- Project creators become admins — Creating a project automatically makes you its admin. This aligns with how runners and automations already work.
- Share with individual users — Admins of projects, runners, and automations can now share directly with individual users. No group required.
- Share with existing groups — Previously, only org admins could share resources with groups. Now any resource admin can share with groups, even if they are just a member of the organization.
Announcement Banner
Organization admins can now display announcement banners to communicate important information to all organization members directly within the dashboard.What’s new:- Admin settings page: Configure banners from Settings → Organization → Announcements
- Markdown support: Format messages with bold, italic, and links
- Live preview: See exactly how your banner will appear before publishing
- Toggle control: Quickly enable or disable the banner without losing your message
- Navigate to Settings → Organization → Announcements
- Enable the announcement banner toggle
- Enter your message (up to 1,000 characters)
- Click Save to publish
CLI: Action Required - Force Update
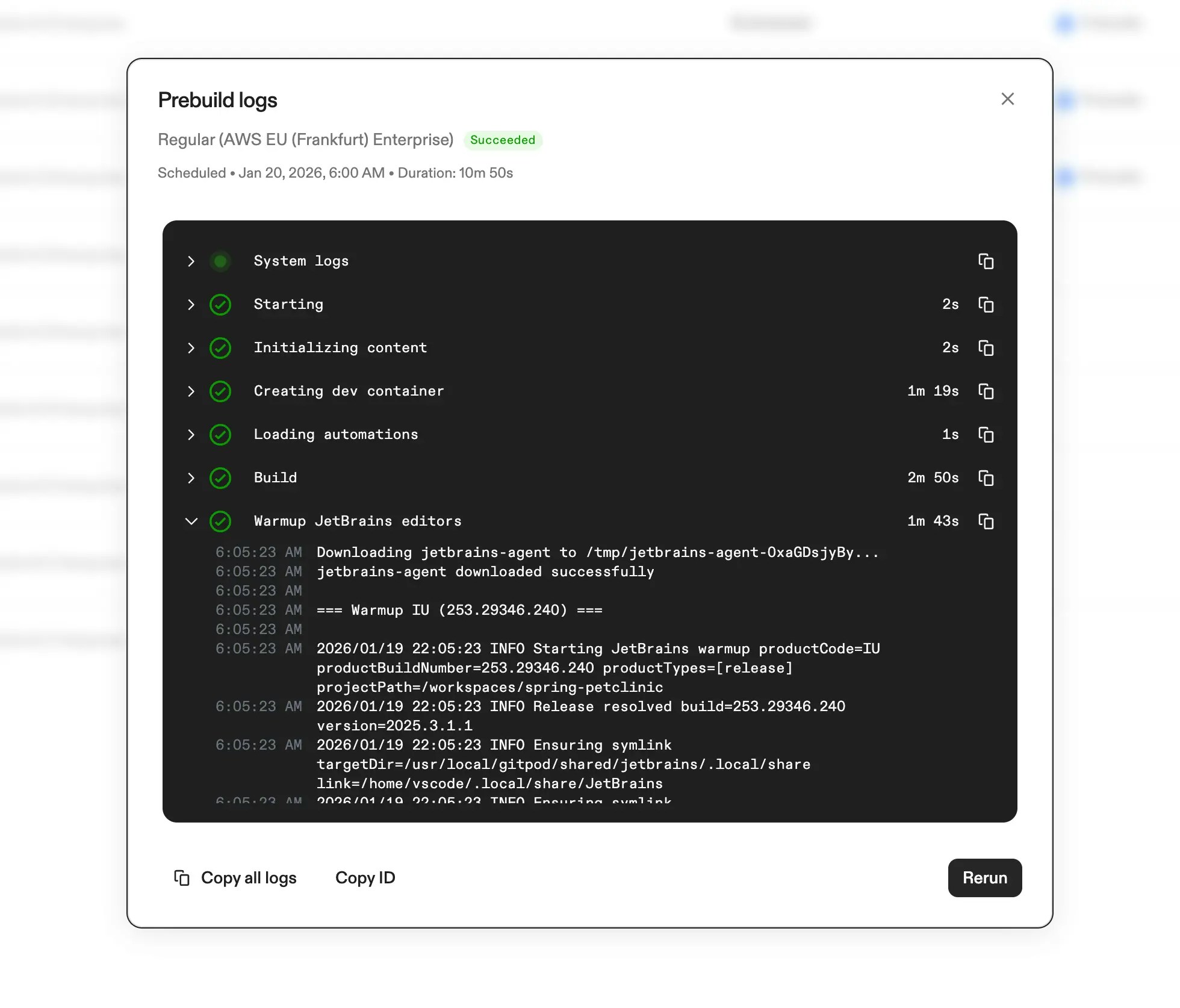
A recent CLI release contained a version format issue that breaks automatic updates. If your CLI shows a version likemain-gha.XXXXX when running gitpod version, auto-update will not work.To fix, run:gitpod version should show a version in the format YYYYMMDD.HHMM.N (e.g., 20260120.0512.0).Read more about the CLI in its documentation.JetBrains Warmup for Prebuilds
Prebuilds now support JetBrains warmup, significantly reducing editor startup time for JetBrains users. When enabled, prebuilds download and install the JetBrains backend and build project indexes ahead of time.What’s new:- Backend pre-installation: JetBrains backend is downloaded and installed during prebuilds
- Index building: Project indexes are built during prebuilds using the JetBrains warmup command
- Recommended editors: Configure which editors to recommend for your project, which also determines which JetBrains editors to warm up
- Skip editor backend download when opening JetBrains editors
- Instant code navigation and analysis with prebuilt indexes
- Consistent experience across all team members
- Enable JetBrains warmup in your project’s prebuild configuration
- Configure recommended editors to specify which JetBrains editors to warm up
- Trigger a prebuild to create a warmed-up snapshot
Claude Opus 4.5 for Ona Cloud
Ona Cloud users now have access to Claude Opus 4.5 for new agent conversations. This model upgrade brings improved reasoning and code generation to your development workflows.What’s new:- New agent conversations on Ona Cloud now use Claude Opus 4.5
- Existing conversations continue with their original model
- Start a new conversation with Ona Agent to use Claude Opus 4.5
- Learn more about Ona Agents
Agent Skills support
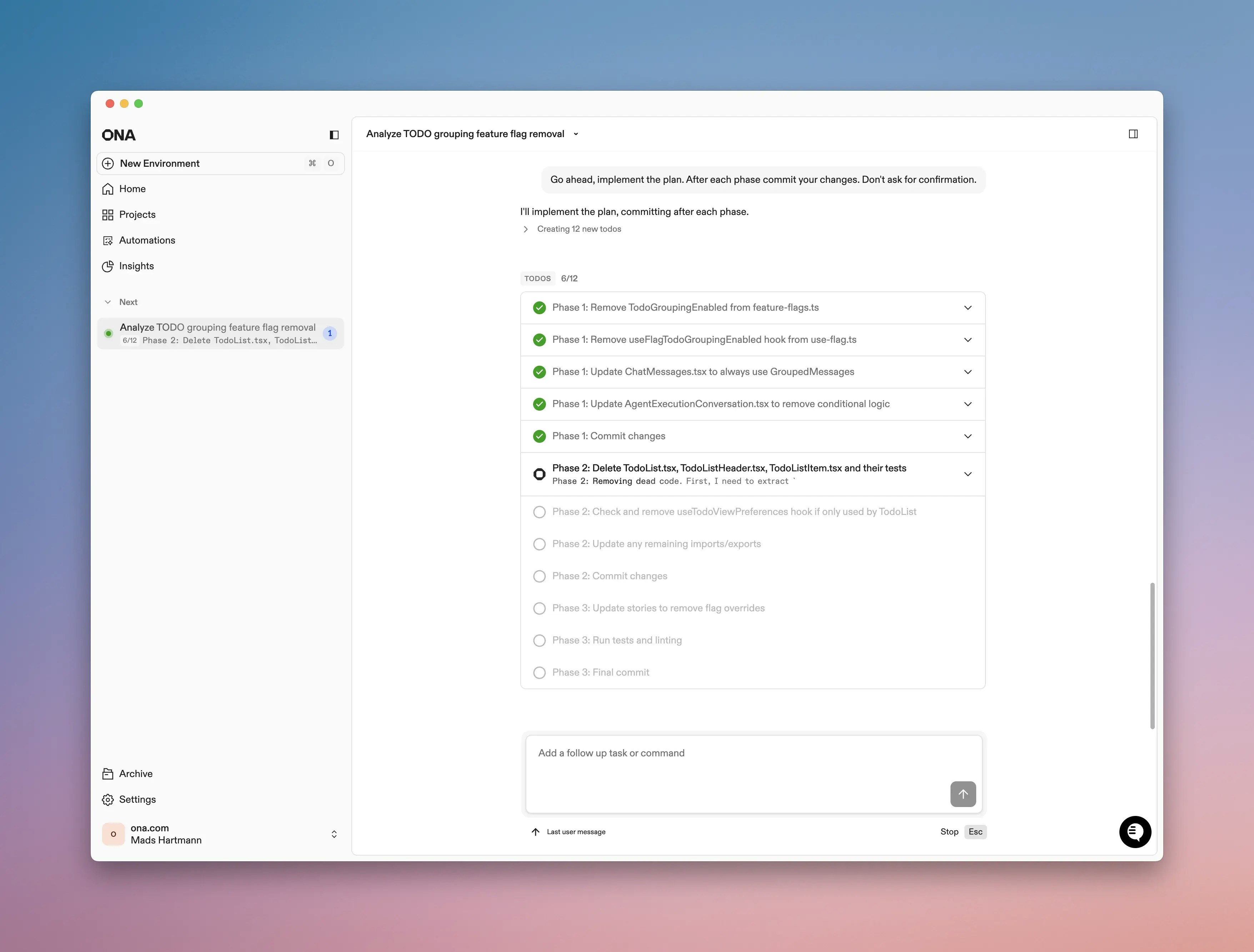
Ona Agent now supports Agent Skills - an open format for multi-step workflows. AddSKILL.md files to .ona/skills/ and the agent discovers and uses them when relevant.Learn more about skillsTODO grouping in conversations
Ona Agent conversations now group TODO items together, making it easier to follow the agent’s progress on multi-step tasks.What’s new:- Grouped display: TODOs created together appear in a single collapsible container
- Progress tracking: See at a glance how many tasks are completed (e.g., “3/5”)
- Status indicators: Each TODO shows its current state—pending, in progress, or done
- Expandable details: Click any TODO to see the work performed under it
- Live updates: Watch the agent’s progress in real-time as it works through each item
Security Agents now generally available
Security Agents configuration is now available to all organizations in Settings > Policies, allowing you to enable CrowdStrike Falcon protection for your workspaces.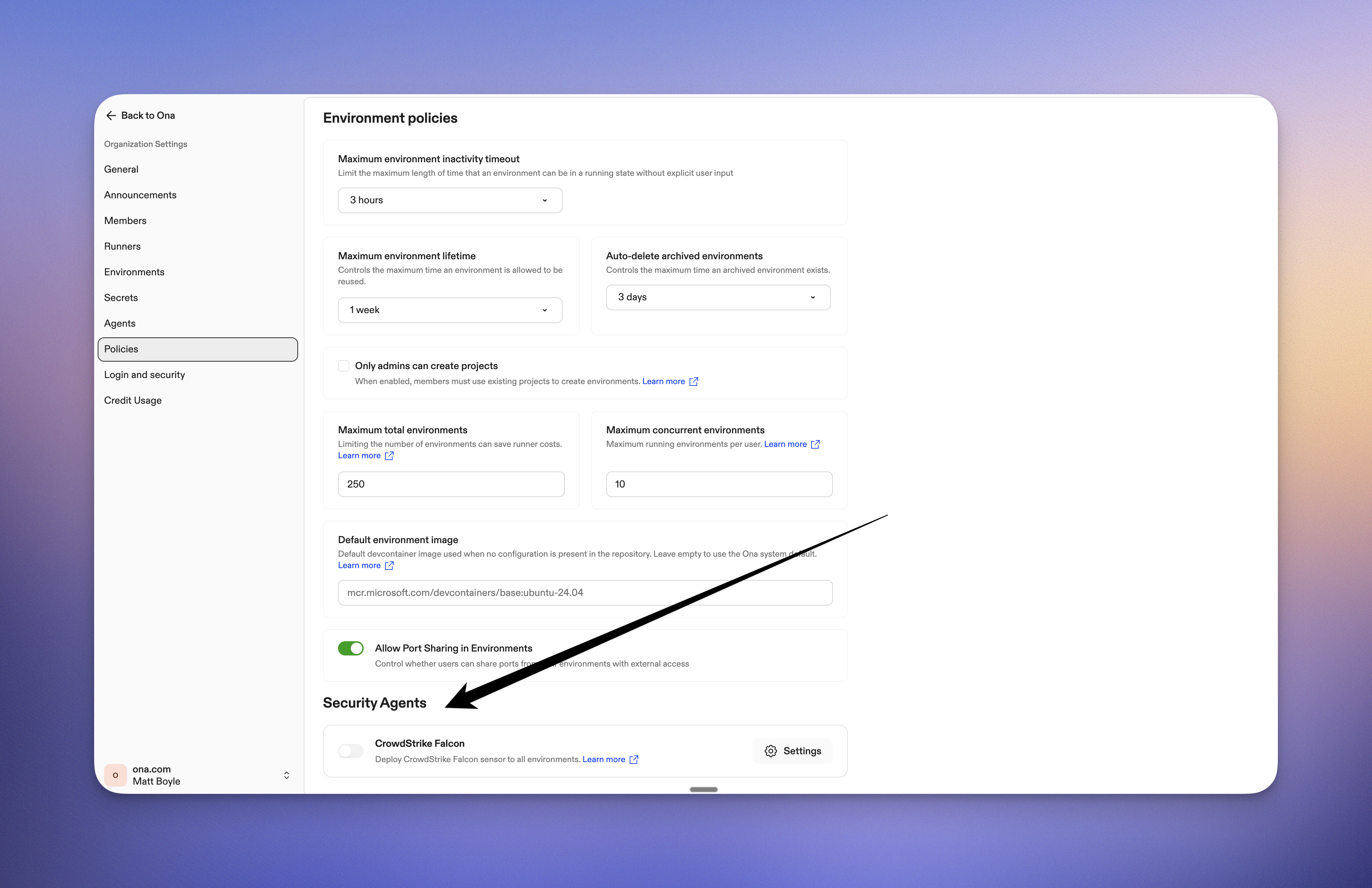
CLI improvements
The CLI continues to get more powerful with new commands and quality-of-life improvements.New commands:gitpod environment keep-alive— Prevent automatic shutdown during long-running tasks by watching a process or PIDgitpod logout— Sign out of the CLIgitpod network-troubleshoot— Diagnose connectivity issuesgitpod user dotfiles— Manage your dotfiles configuration
- Running
gitpod env sshwithout specifying an environment now shows an interactive picker - Stopped environments automatically start when you connect via SSH
--param key=valueforai automation start— Pass parameters to automations--phaseforenvironment list— Filter by phase (running, stopped, etc.)--nameforenvironment create— Set a custom environment name
Recommended editors
Projects can now configure recommended editors in project settings. Users will see these as recommended options when opening environments, and this also determines which JetBrains IDEs are warmed up during prebuilds.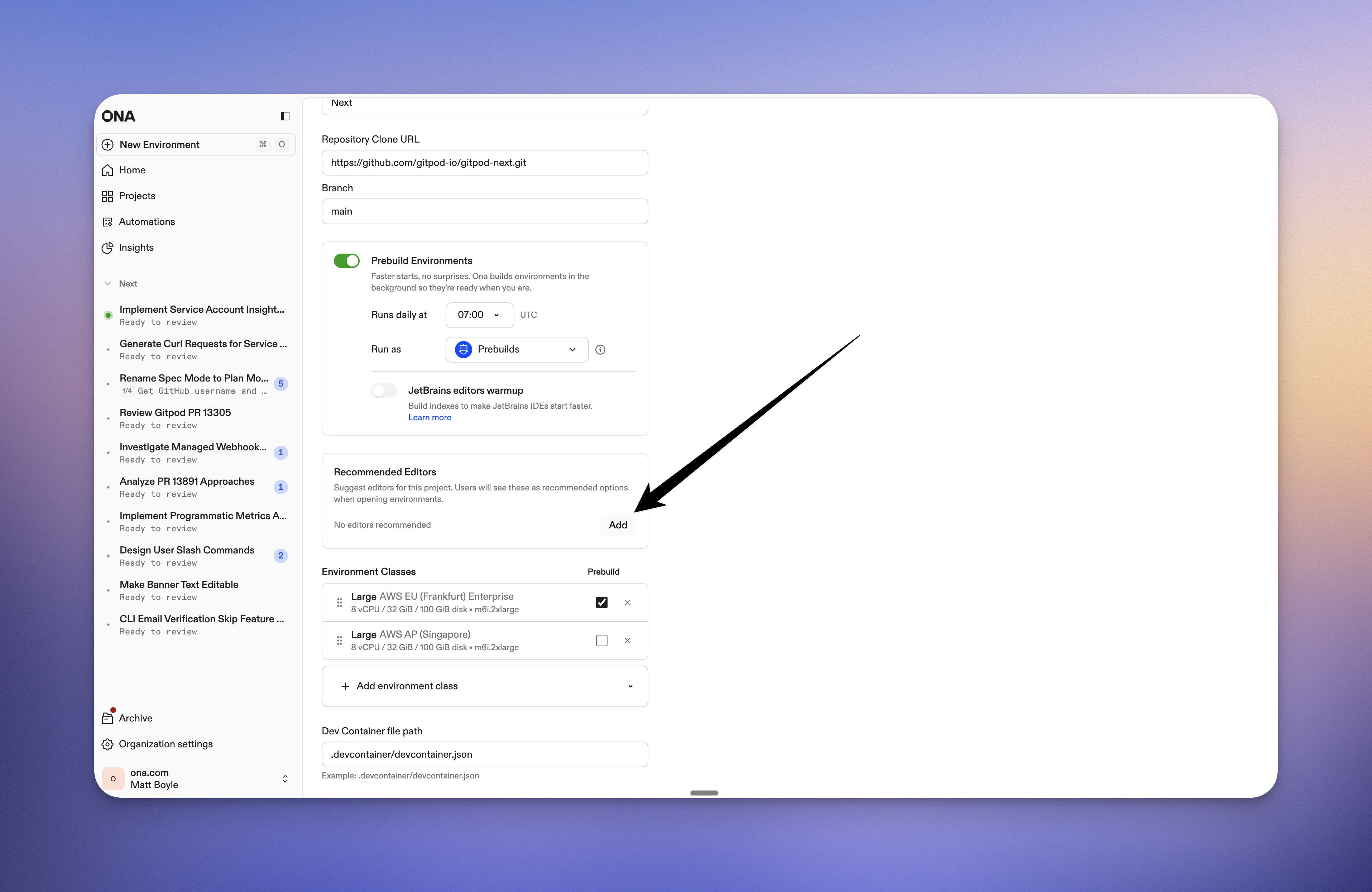
Before-snapshot automations
Automations now support abefore_snapshot trigger type. Use this to run cleanup tasks, update dependencies, or perform other operations automatically before an environment snapshot is created.Other improvements
- Markdown files now show a rendered preview in the diff viewer.
- Snapshot progress displays completion percentage during snapshotting.
- “Ask Ona” button appears on devcontainer build failures for quick troubleshooting.
- New split button for selecting editor versions.
- New modal for upgrading AWS EC2 runners.
- New account settings modal for managing personal settings.
- Prompt input, contexts, and environment class persist across sessions.
- VS Code Browser and agents are now exempt from port sharing policy by default.
- Audit logs now include login and logout events (Enterprise).
- Email invites show pending status and warn before navigating away with unsent invites.
- Ona Agent no longer returns 502 errors with Claude Opus 4.5 or Sonnet 4.5 when provider fallback is enabled.
- Ona SWE no longer fails when Anthropic environment variables are set in your workspace.
- SCP file transfers no longer fail over slow networks.
- Hosted compute now allows exposing ports 1024-2999 (previously only 3000+).
December 2025
Prebuilds now available on GCP
Prebuilds are now supported on GCP Enterprise runners. Teams running Ona on Google Cloud infrastructure can now use prebuilds to reduce environment startup times.Requirements:- Update your Terraform stack to the latest version to enable snapshot permissions
Ona now integrates with Linear
Ona agents can now connect with Linear to manage your project tasks directly from your development environment.What you can do:- Create and manage issues: Ask agents to create Linear issues from code, errors, or conversations
- Search and filter: Find issues by status, assignee, labels, or content
- Update metadata: Add comments, change status, update labels, and assign issues
- Access project context: Retrieve project information to inform development decisions
- Organization setup: Admins enable integrations at the organization level
- User authentication: Individual users authenticate to grant agents access to their accounts
- Natural interaction: Simply ask your agent to perform actions—no special commands needed
- “Create a Linear issue for this bug with steps to reproduce”
- “Show me all high-priority issues assigned to me”
- “Update issue ABC-123 to mark it as in progress”
Custom domains for secure management plane access
Enterprise customers can now access the Ona management plane through their own custom domain with full TLS termination. This enables organizations to route all traffic through their controlled infrastructure, meeting strict security and compliance requirements.Why this matters:- Security control: All traffic to the management plane flows through infrastructure you own and manage
- Compliance ready: Meet organizational requirements for domain ownership and traffic routing
- SSO integration: Works seamlessly with your existing Single Sign-On configuration
- Enforcement options: Optionally block access via the default domain, ensuring all users go through your custom domain
- AWS: Uses VPC Endpoints and Network Load Balancer for private connectivity
- GCP: Uses Private Service Connect (PSC) and regional HTTPS Load Balancer with support for both internal (private) and external (public) load balancer configurations
- Register your custom domain in the Ona dashboard with your cloud provider details
- Deploy the required infrastructure in your AWS or GCP account
- Configure DNS to point your domain to the load balancer
- Optionally enforce custom domain access for all users
- Review the Custom domain documentation for setup instructions
- For GCP deployments, contact Ona support to get access to the Terraform module
Enterprise Runner now available in AWS Paris (eu-west-3) region
The Ona Enterprise Runner is now available in the AWS Paris (eu-west-3) region, expanding deployment options for teams requiring data residency in Western Europe.Why this matters:- Regional compliance: Meet data residency requirements for France and the EU
- Lower latency: Improved performance for teams based in Western Europe
- Enterprise ready: Full Enterprise Runner capabilities including AI agent integration and direct connectivity
- Flexible deployment: Deploy in your VPC with custom networking configurations
- Contact sales to enable Enterprise Runner
- Follow the AWS Enterprise Runner setup guide
- Configure your runner to use the eu-west-3 region
Extended Single Sign-On (SSO) support
- Multiple email domains per login provider: Configure several email domains for a single identity provider, ideal for organizations with multiple subsidiaries or acquired companies
- Multiple identity providers per organization: Set up more than one identity provider (e.g., both Okta and Azure AD) to accommodate different teams or authentication requirements
- Cross-organization domain support: Use the same email domain across different organizations—users are presented with a list of login options to select their organization
- Enterprise flexibility: Large organizations with complex structures can now centralize authentication across all their domains
- M&A ready: Easily onboard acquired companies without forcing immediate identity provider migrations
- Multi-team support: Accommodate different authentication requirements for employees, contractors, and partners within the same organization
- Navigate to Settings → Organization → SSO
- Add additional email domains to existing login providers or configure new identity providers
- Learn more in our SSO documentation
Run prebuilds as service accounts
Prebuilds can now run as service accounts, decoupling prebuild execution from individual user accounts. This ensures prebuilds continue working regardless of user availability or permission changes.What’s new:- Configure the prebuild executor in project settings
- Choose between a user (default) or a service account
- Prebuilds no longer break when team members leave or change roles
- Dedicated credentials for prebuild execution
Automation logs in prebuilds
Prebuild logs now include output from automation tasks, making it easier to debug prebuild failures and understand what ran during prebuild execution.See Viewing Logs for details.November 2025
Editor version restrictions for organization policies
Organization administrators can now restrict which versions of editors their team can use, in addition to controlling which editors are available. This provides greater control over development environment consistency and security.Why this matters:- Stability: Standardize on tested versions before adopting the newest releases
- Security: Control version updates to verify security patches before organization-wide deployment
- Compatibility: Ensure all team members use versions tested with your workflows and integrations
- Configure version restrictions in the same “Manage Editors” dialog as editor restrictions
- Currently available for JetBrains IDEs (IntelliJ IDEA, PyCharm, GoLand, etc.)
- Users attempting to use non-allowed versions automatically fall back to the latest allowed version
- Navigate to Settings → Organization → Policies
- Click “Manage Editors” and select the specific versions you want to allow
- Learn more in our Organization Policies documentation
Prebuilds: Faster environment startup times
Prebuilds reduce environment startup times by pre-executing your Dev Container build, lifecycle commands, and automation tasks. When you create an environment from a project with prebuilds enabled, it starts from a snapshot instead of running the full setup process.How it works:- Configure prebuilds at the project level with a daily schedule
- Prebuilds run your Dev Container build,
onCreateCommand,updateContentCommand, and automation tasks with theprebuildtrigger - A snapshot is created and used for all new environments from that project
- Prebuilds are automatically deleted after 7 days
- AWS Enterprise runners
- GCP Enterprise runners
- Ona Cloud
- Ona Cloud: Environment usage is billed normally during prebuild creation. Snapshot storage is currently free (pricing may be introduced in the future).
- Enterprise: You pay for compute resources during prebuild creation and storage costs for the snapshot. Storage is billed only for actual data stored (e.g., 50GB used on a 100GB volume = 50GB billed).
Ona Agents now available on GCP Runner
Ona Agents are now fully supported on GCP Runner, bringing AI-powered development assistance to your Google Cloud infrastructure. Teams using GCP Runner can now leverage Ona Agents to accelerate development with up to 4x productivity gains—all while keeping code and data secure within your VPC.Why this matters:- AI-powered development in your VPC: Use Ona Agents with the same security and compliance benefits of GCP Runner
- Flexible LLM options: Configure Google Vertex AI or other supported LLM providers to power your agents
- Enterprise-grade control: Maintain full control over your AI infrastructure with your own LLM provider
- Seamless integration: Agents work natively with your GCP Runner environments
- Contact sales or reach out to your account executive to enable GCP Runner with Ona Agents
- Review the GCP Runner overview and setup guide
- Learn about Ona Agents and supported capabilities
- Configure your LLM provider (Google Vertex AI recommended for GCP)
Organize teams and control access with Groups
Ona now supports Groups, giving you fine-grained control over who can access projects and runners in your organization. Organize teams by function or infrastructure needs, add members, and share resources with them.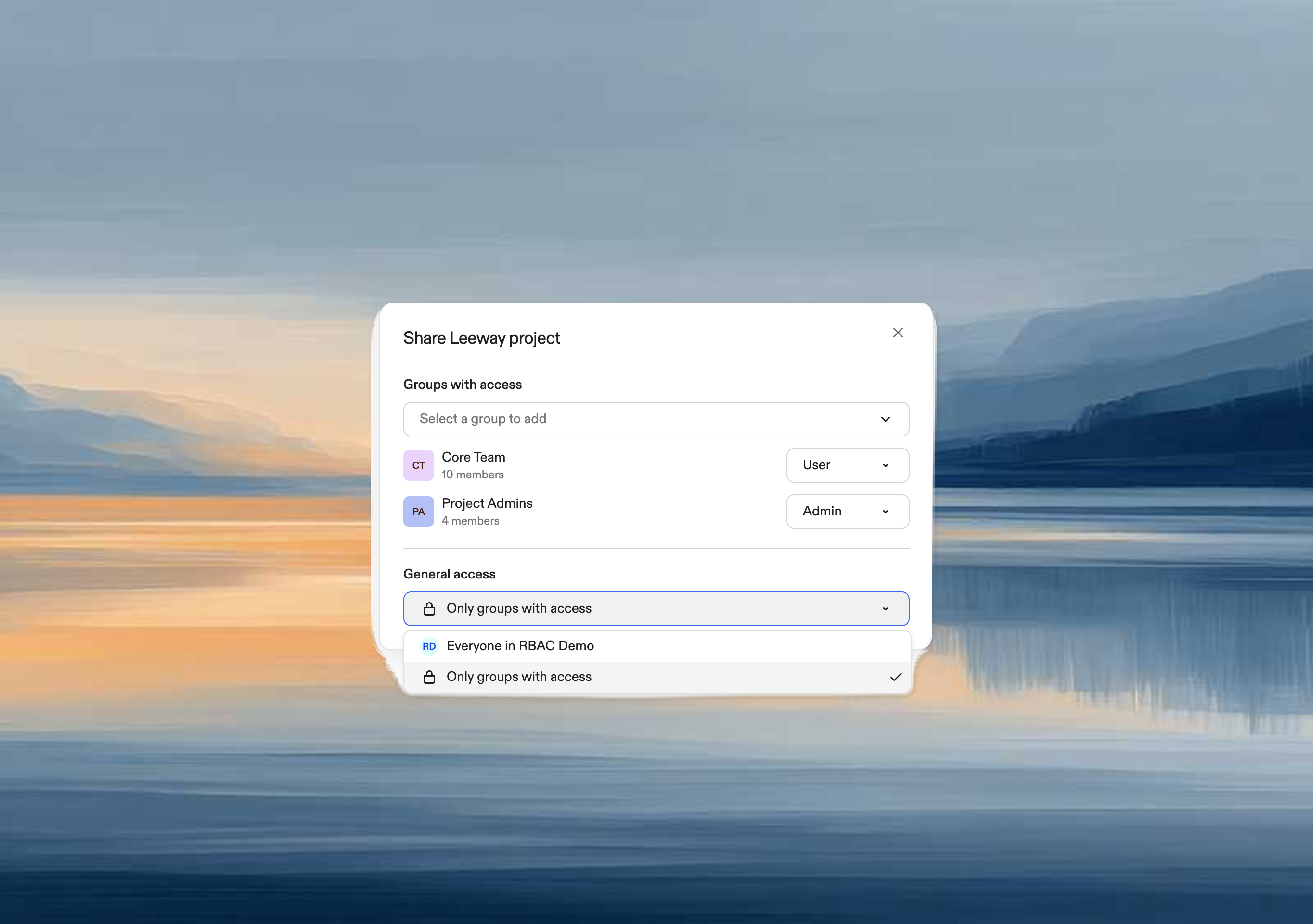
- Keep workspaces focused: Developers see projects relevant to their work, not everything
- Share smarter: Give the right access without making everyone an admin
- Support compliance: Route EU developers to EU runners, ML engineers to GPU infrastructure
- Create groups in Settings → Members → Groups
- Share projects and runners with specific groups using the Share dialog
- Assign role-based permissions: User (view/use), Editor (manage), or Admin (full control)
- Built-in warnings prevent access issues when projects and runners aren’t aligned
October 2025
Enterprise Runner now available in AWS Mumbai (ap-south-1) region
The Ona Enterprise Runner is now available in the AWS Mumbai (ap-south-1) region, expanding deployment options for teams requiring data residency in South Asia.Why this matters:- Regional compliance: Meet data residency requirements for India and South Asia
- Lower latency: Improved performance for teams based in the region
- Enterprise ready: Full Enterprise Runner capabilities including AI agent integration and direct connectivity
- Flexible deployment: Deploy in your VPC with custom networking configurations
- Contact sales to enable Enterprise Runner
- Follow the AWS Enterprise Runner setup guide
- Configure your runner to use the ap-south-1 region
Ona is now Available in Google Cloud.
We’re expanding where great software gets built. From today, Ona can also run natively in Google Cloud, in your VPC.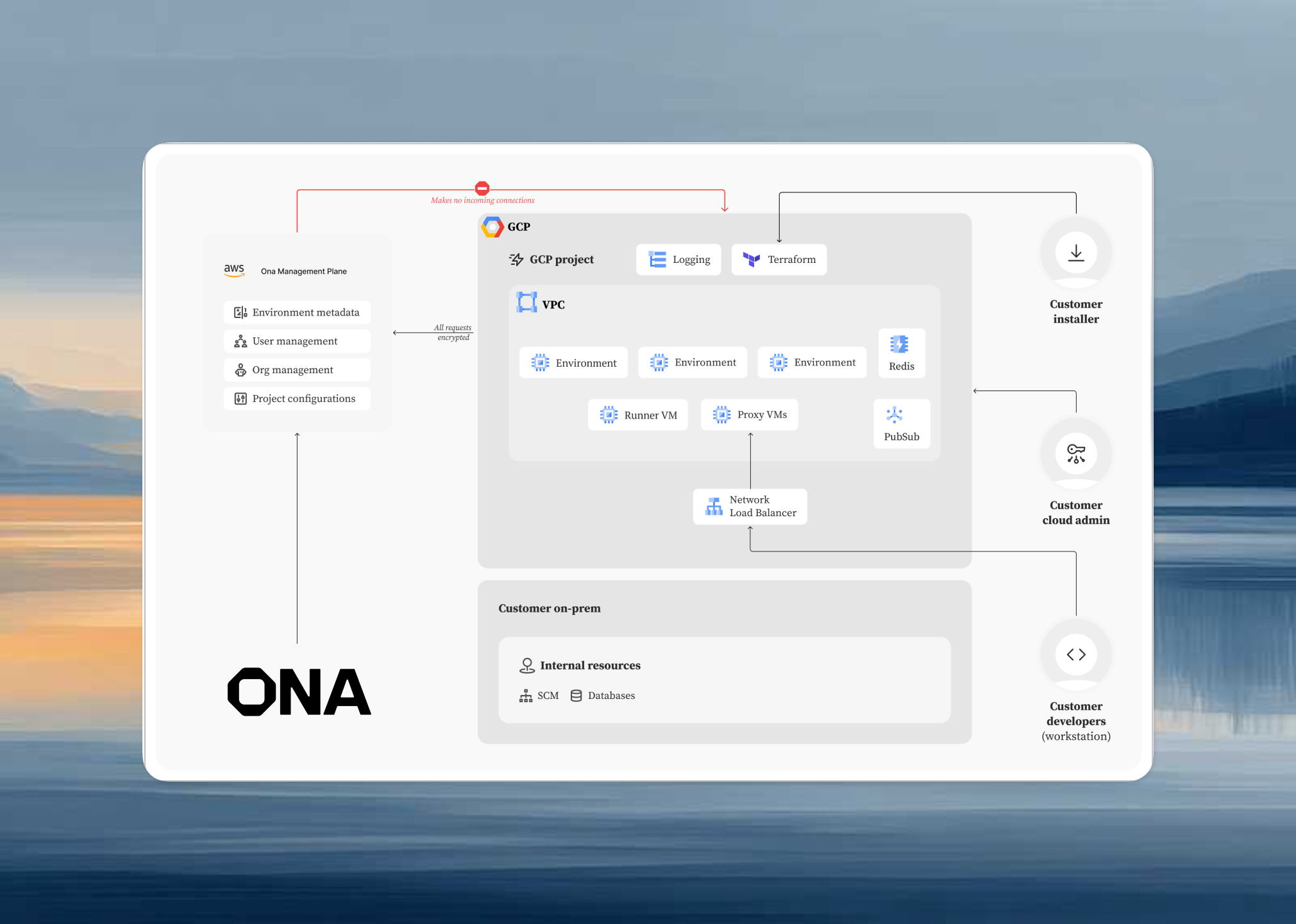
- Get started in minutes: a Terraform apply stands up everything you need.
- Keep traffic where you want it: external or internal HTTPS load balancing.
- Use your standards: CMEK, proxy, custom images, labels, enterprise IAM.
- Ship faster: native access to private GAR images, observability out of the box.
- Agent Ready: Google Cloud is Ona Agents ready. Learn how to use Ona Agents and join our customers in getting up to 4x more productivity.
- Contact sales to enable Enterprise
- Follow the GCP Runner setup and read the Overview
View and Review Code changes directly from mobile
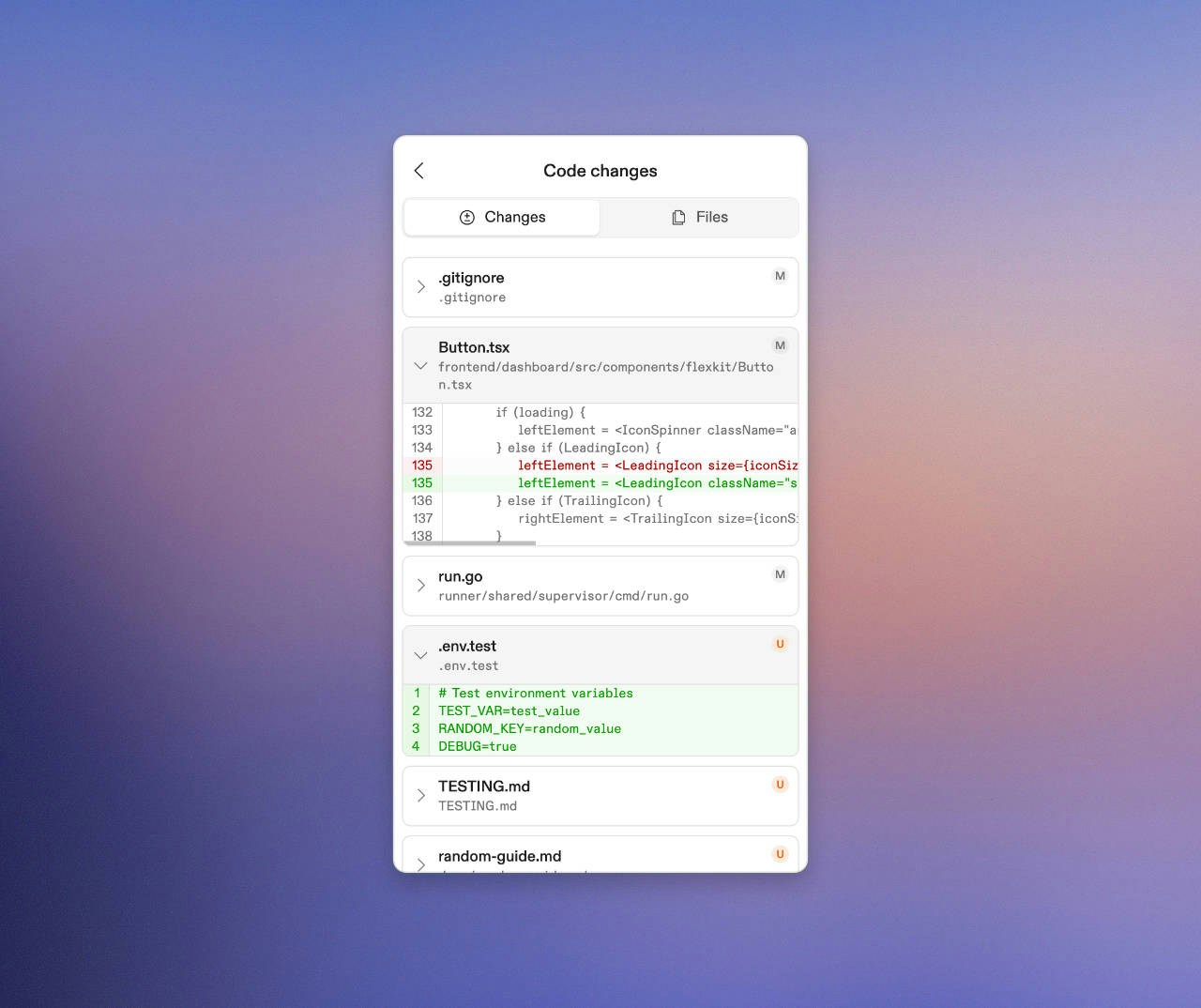
- The “Changes” tab shows you a list of changed files in the environment. You can expand each file to view the diff of the file.
- The “Files” tab gives you a tree view of all the changed files, which you can use to navigate to the diff of the file you want.
Visualize architecture and workflows with Mermaid diagrams
Ona Agent can now generate and render Mermaid diagrams directly in conversations, making it easy to visualize system architecture, dependencies, workflows, and data relationships without leaving your development environment.How to use:Simply ask Ona Agent to create diagrams using natural language:- Draw an architecture diagram showing how our microservices communicate
- Create a sequence diagram for the authentication flow
- Generate an ER diagram for our database schema
- Flowcharts and decision trees
- Sequence diagrams
- Class diagrams
- Entity-relationship diagrams
- State diagrams
- Gantt charts
- Git graphs
September 2025
Claude Sonnet 4.5 now available
Claude Sonnet 4.5 is now available in Ona, bringing enhanced reasoning capabilities and improved code generation to your development workflow.How to enable Sonnet 4.5:- Free and Core tiers: Sonnet 4.5 is automatically available, no setup or changes are required
- Enterprise tier: Organization admins can configure your LLM provider by selecting Sonnet 4.5 in the settings for each runner. Ensure you are on the latest runner version runner to update. Please note that the removal of a previous LLM integration on a runner will break existing conversations.
- LLM Providers Overview
- Anthropic Configuration
- AWS Bedrock Configuration
- Google Vertex AI Configuration
-
Updating AWS Runner
Encode your expertise into slash commands
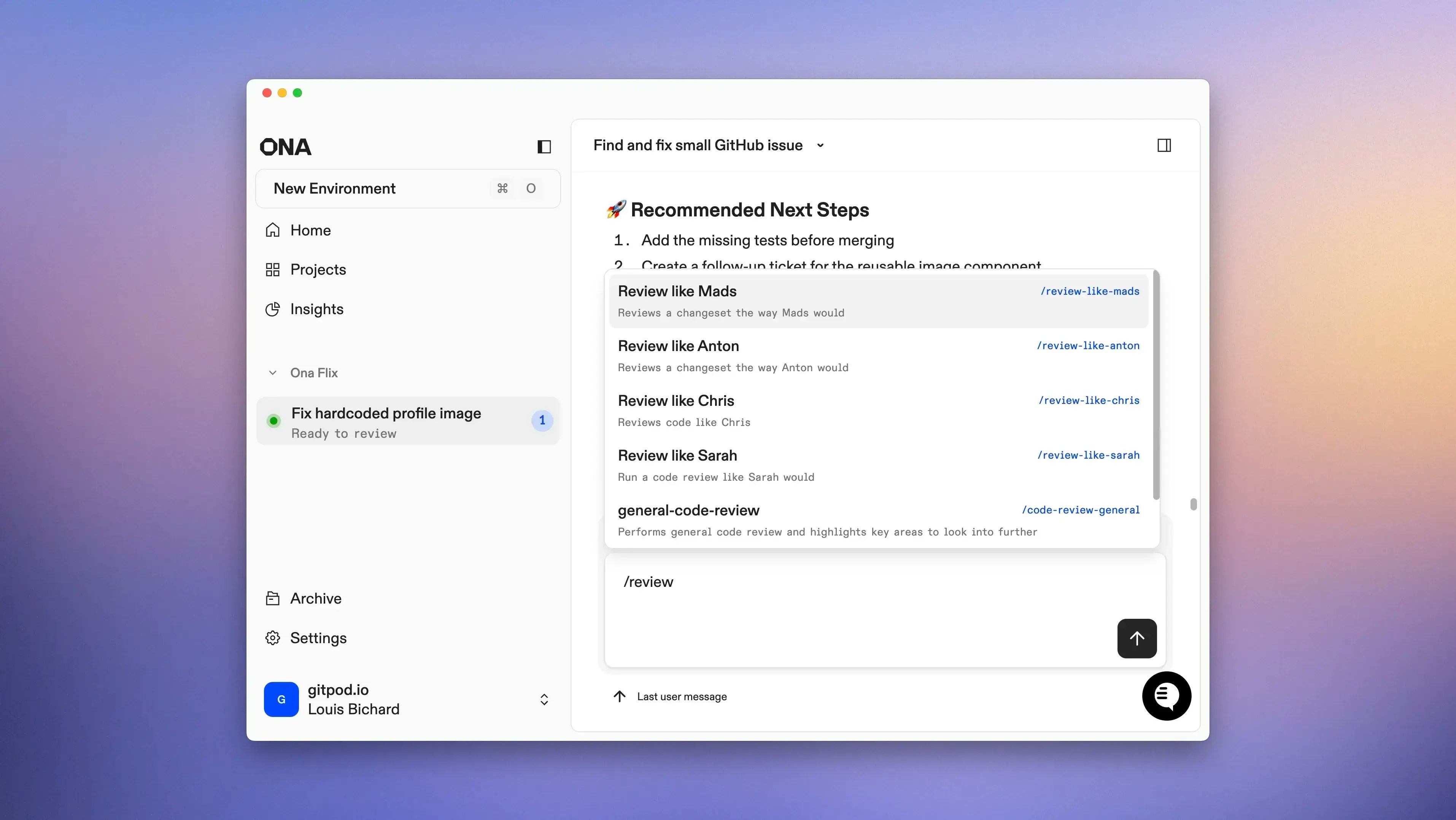
- Ensure everyone follows the same PR format or review process
- Capture your best reviewer’s approach in commands like
/review-like-sarah - Automate common tasks like
/pr,/fix-ci-build, or/weekly-digest
/test can run against real databases and integrations and /fix-ci-build has everything it needs to succeed. All environments are isolated so there’s never the risk of breaking your laptop or your flow.For more, see the skills docs and our best practices guide.Track agent progress with todos
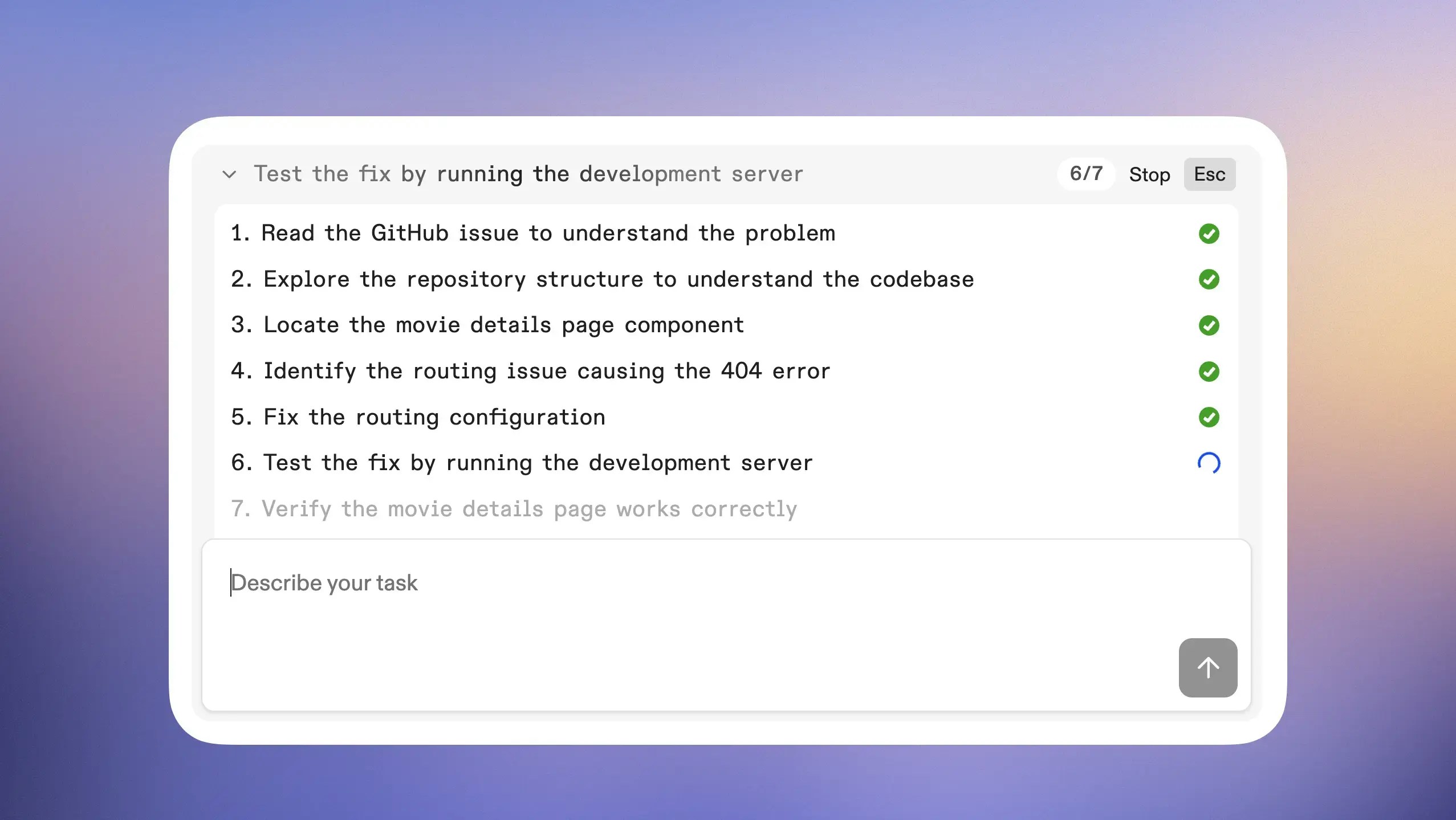
- See the plan at a glance instead of reading through detailed agent output
- Quickly spot when an agent might need steering without monitoring every action
- Add, remove, or modify todos mid-task to adjust your agent’s approach
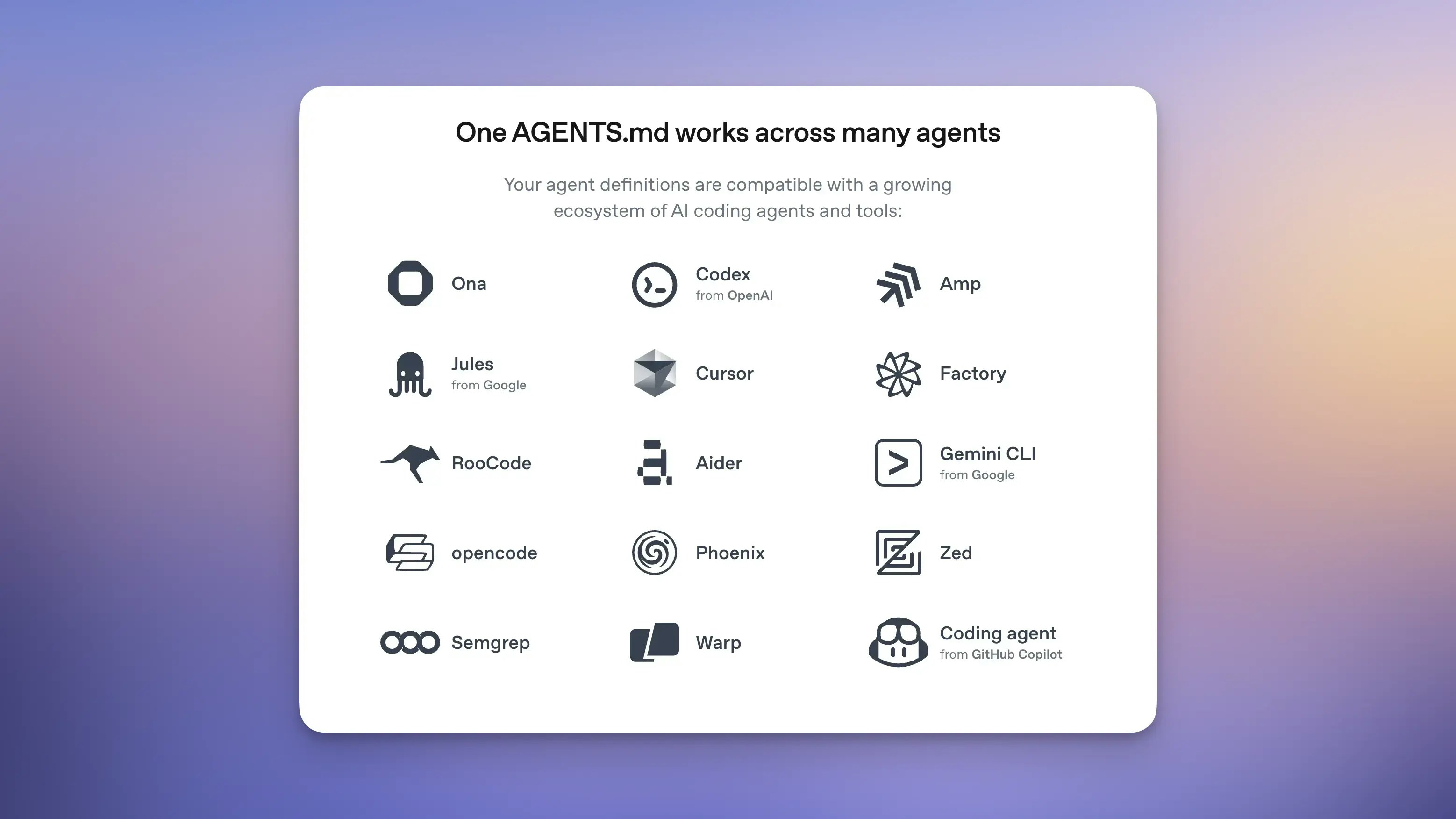
Ona now supports AGENTS.md
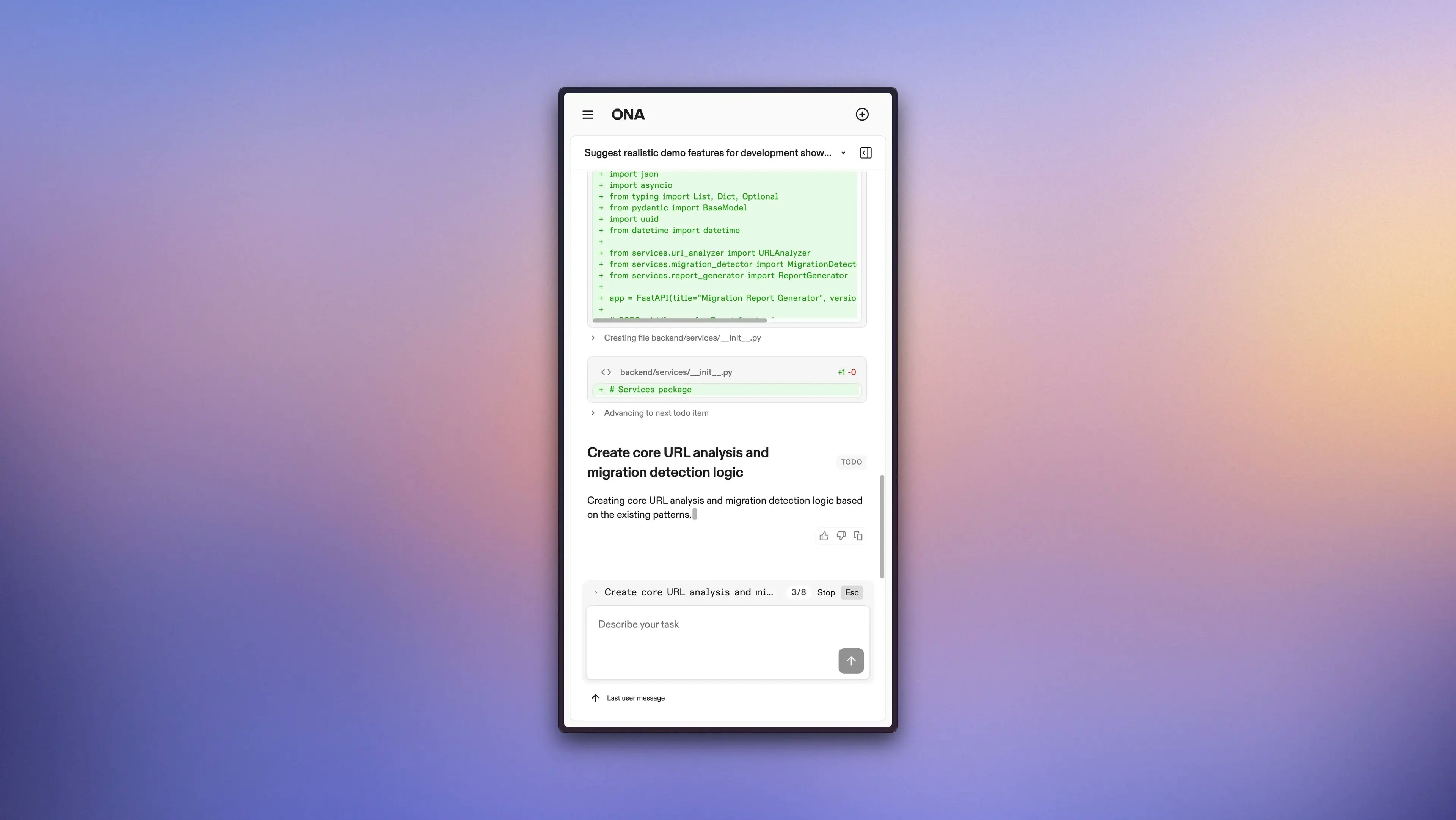
Keep momentum on any device from mobile to iPad
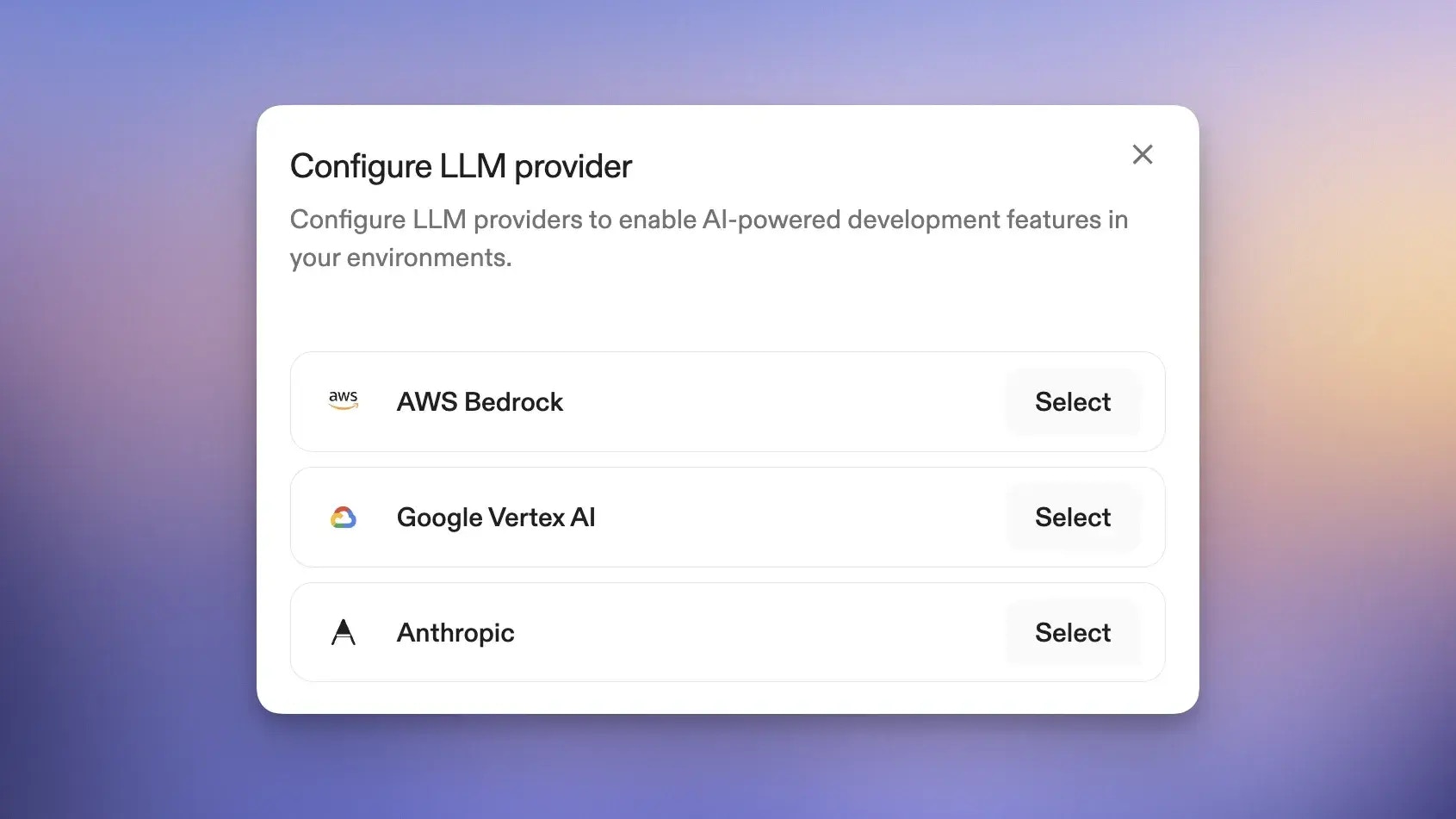
Privacy-first coding agent inference with Bedrock and Vertex
Sandboxed AI software development with Dev Container
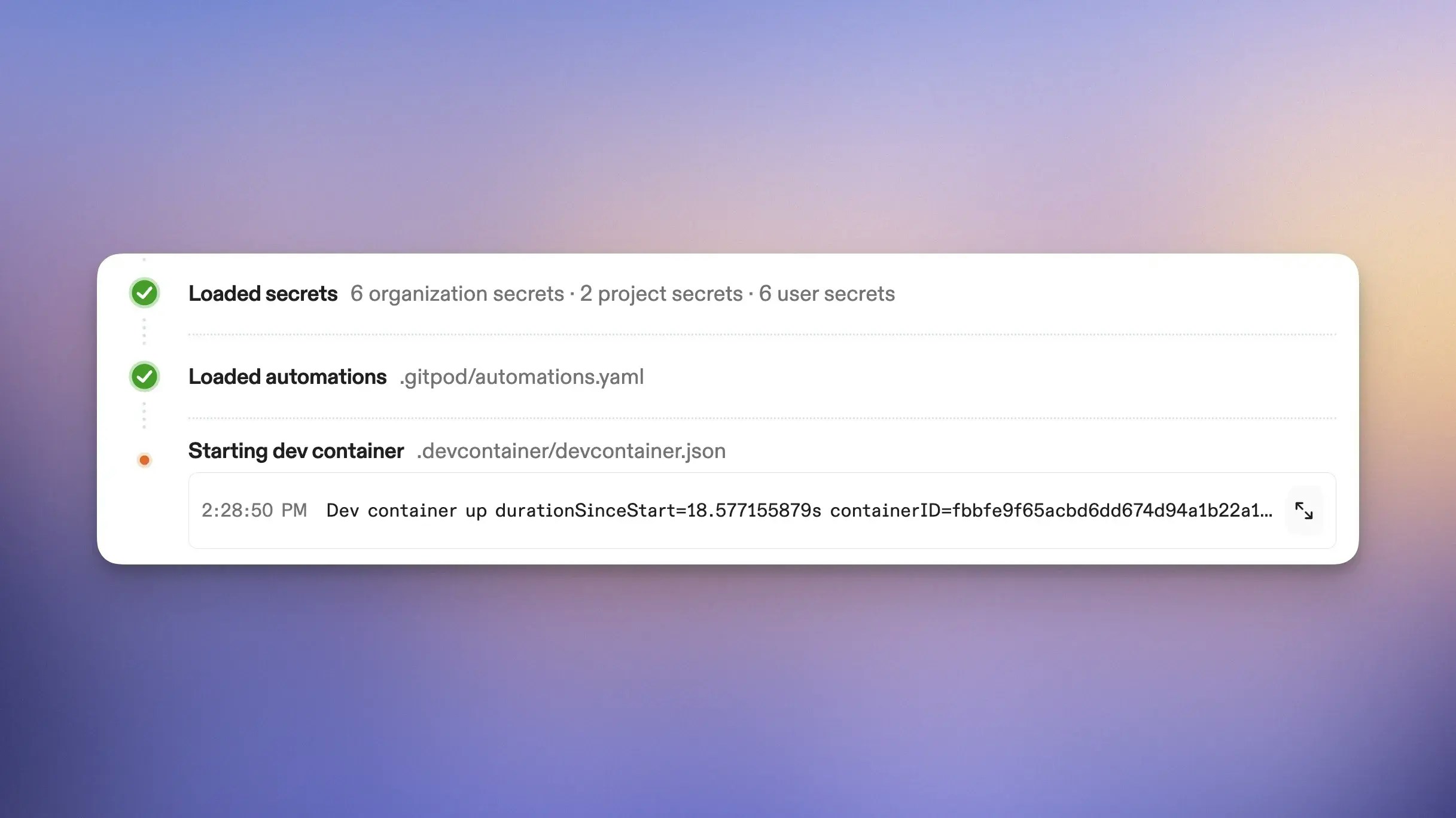
- Complete agent isolation: Each agent runs in its own Dev Container with OS level isolation, preventing cross-contamination between source control and projects.
- Ephemeral by design: Environments are created newly for each task (e.g. issue, bug, feature) and destroyed on completion, ensuring no persistent attack surface.
- Standardized environments: Dev Containers are defined in code and pre-configured with your exact dependencies and access credentials.
August 2025
Standardized JetBrains plugin management via devcontainer.json
You can now configure JetBrains IDE plugins directly in your devcontainer.json file, enabling fully standardized plugin management across development environments.This update lets teams pre-install essential plugins from the JetBrains Marketplace using their plugin IDs, ensuring consistent tooling for all team members. It eliminates the need for manual plugin installation, reducing setup time and improving onboarding speed.Key capabilities:- Plugin installation: Specify plugin IDs from the JetBrains Marketplace for automatic installation.
- Team consistency: Guarantee the same set of plugins across every developer environment.
- Faster onboarding: Remove the manual step of plugin setup for new contributors.
devcontainer.json
July 2025
HTTPS support for environment services via port sharing
You can now expose environment services over HTTPS using Gitpod’s port sharing feature. This enables secure communication with applications running in your environment, which is ideal for testing HTTPS-only setups or integrating with services requiring encrypted transport.What’s new:- UI integration: Select https as the protocol in the port sharing dialog
- CLI support: Use
--protocol httpswithgitpod environment port opento expose environment service ports securely.
- Applications with HTTPS-only redirects or policies
- Streaming APIs requiring secure connections
Support for multiple region-aware environment classes per project
We’re excited to announce that Gitpod now supports Multiple environment classes for a project, a highly requested feature that enhances reliability and flexibility for organizations.With this new feature, you can:- Configure up to 30 environment classes per project, providing built-in regional redundancy
- Set a default environment class while offering alternatives for user selection
- Avoid creating multiple projects for the same repository across different regions
- Benefit from automatic fallback options when a preferred environment class is unavailable
- Enhanced Resilience: Eliminate single points of failure with multiple region support in a single project
- User Flexibility: Users can select their preferred environment class through an intuitive UI
- Intelligent Fallback: When a selected environment class is unavailable, users receive informative error messages and alternative options
- Preference Persistence: The system remembers user preferences for future project launches
- Simplified Project Management: Reduce project proliferation by consolidating multi-region support
Archive & Auto-delete for Environments
We’re excited to announce Archive & Auto-delete, a new feature that automatically manages your environment lifecycle to help reduce storage costs.With this new feature, you can:- Automatically archive inactive environments after 7 days of inactivity
- Configure auto-deletion policies to remove archived environments after 1, 2, or 4 weeks
- Set organization-wide retention limits to ensure consistent storage management
- Two-stage lifecycle: Environments are archived first (reversible), then auto-deleted based on your preferences
- Flexible policies: Users can set preferences within organization-defined limits
- Bulk management: Delete all archived environments at once with safety controls
- Visual indicators: Archive badge shows when you have archived environments
Organization Secrets support
We’re excited to announce that Gitpod now supports Organization secrets, alongside existing User and Project secrets.With this new feature, you can:- Configure organization-wide secrets for all Environments in the organization
- Ensure consistent access to shared credentials and API keys for all team members
- Files: Secrets can be mounted as files for complex structures e.g. JSON.
- Environment Variables: Inject secrets as environment variables.
June 2025
VPC endpoint support for Enterprise AWS runners
Enterprise AWS runners now support VPC endpoints, allowing you to connect to Gitpod’s management plane using AWS PrivateLink.This enhancement provides:- Increased security - All traffic between your runner and Gitpod stays within AWS’s network backbone
- More reliable connectivity - Eliminates dependency on internet routing and potential connectivity issues
- Compliance ready - Ideal for customers with strict security requirements that prohibit internet-bound traffic
- DNS resolution - app.gitpod.io automatically resolves to VPC endpoint IP addresses within your VPC
- AWS PrivateLink - Traffic flows through Amazon’s network infrastructure via VPC endpoints
- Seamless integration - No changes required to your existing runner configuration
- Create an Interface VPC Endpoint in your AWS account pointing to Gitpod’s service
- Configure the endpoint in the same VPC where your runner is deployed
- Enable DNS names for automatic resolution
Enterprise AWS runner with AI agent and direct connectivity
Enterprise AWS Runners are now available for Enterprise customers, providing additional capabilities beyond our AWS Runners.Key features:- Ona AI Agent Integration: AI-powered assistance for automatic Dev Container generation and environment setup
- Direct Connectivity: Bypass Gitpod’s central gateway using your own Network Load Balancer with custom domain and SSL/TLS certificate
- Advanced Networking: Custom VPC configurations with flexible subnet architecture for internal-only or internet-facing deployments
- Flexible Deployment: Deploy behind corporate firewalls with future HTTP proxy support
- HTTP Proxy Support: Custom HTTP proxy configuration for environments behind corporate firewalls
- Custom CA Certificate Support: Integration with enterprise certificate authorities and custom certificate chains
Introducing our AI powered Development Environment setup workflow
Ona’s Enterprise SWE agent, Ona agent, now automatically analyzes repositories and generates Dev Container and automations configurations, helping you discover the value of Gitpod much faster.When developers open an environment without existing Dev Container configurations, Gitpod offers to run our AI powered workflow to generate the configuration automatically.Ona works relentlessly, rebuilding and testing the generated configuration until it is confident it gives you a productive setup.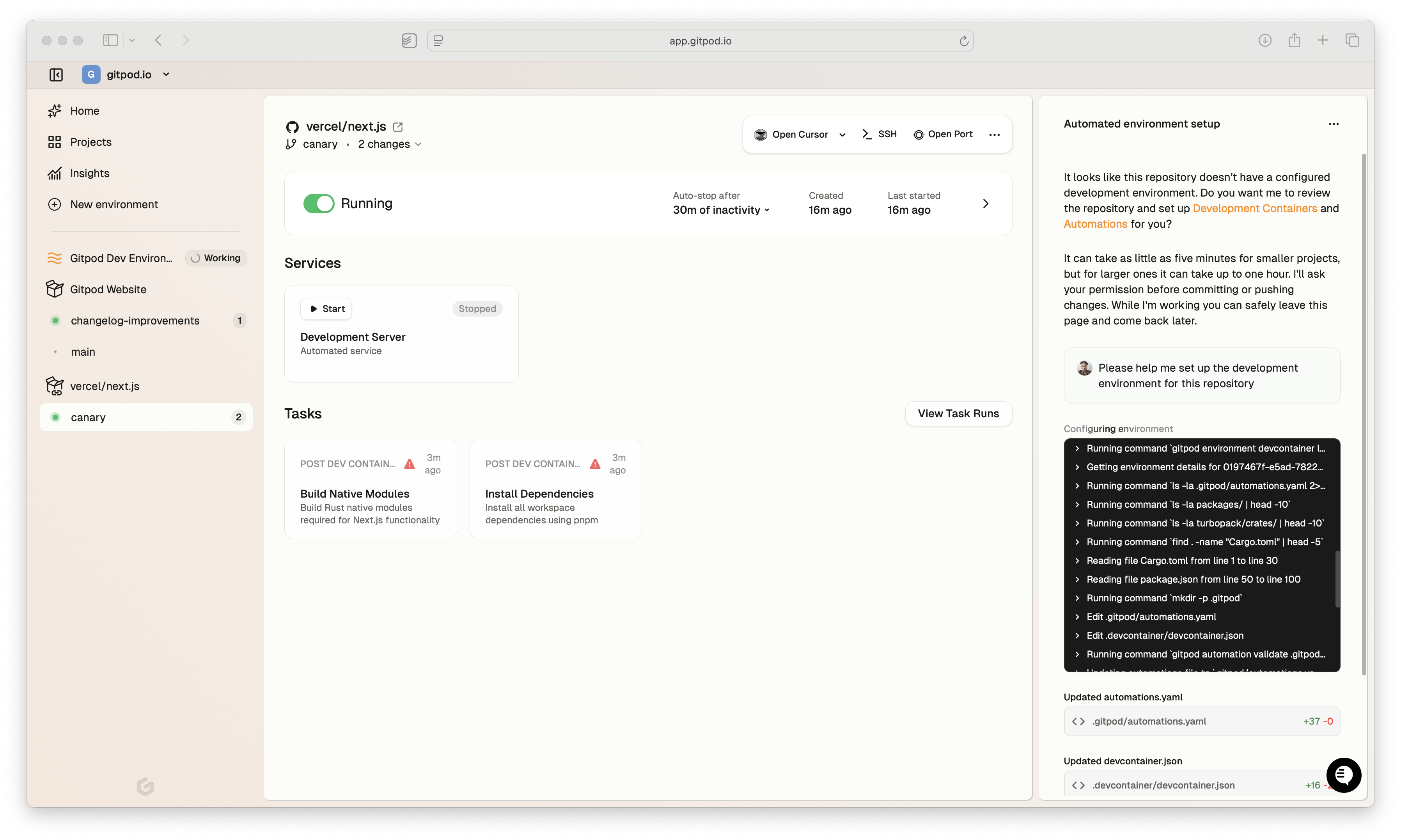
- Open an environment in Gitpod without an existing Dev Container configuration
- Gitpod offers to run our Ona powered setup agent automatically
- Ona generates devcontainer.json and automations.yaml based on detected dependencies and best practices
- Review and commit configurations for your team
- All subsequent environment launches use the optimized configuration
Gitpod now supports Windsurf editor
Gitpod now supports Windsurf as an editor option for your development environments. Windsurf integrates advanced AI capabilities directly into your development workflow, enhancing productivity through natural language interaction and intelligent code assistance. Experience features like Tab-to-Import, real-time linting, and the powerful Cascade AI assistant to streamline your coding process.Using Windsurf with Gitpod: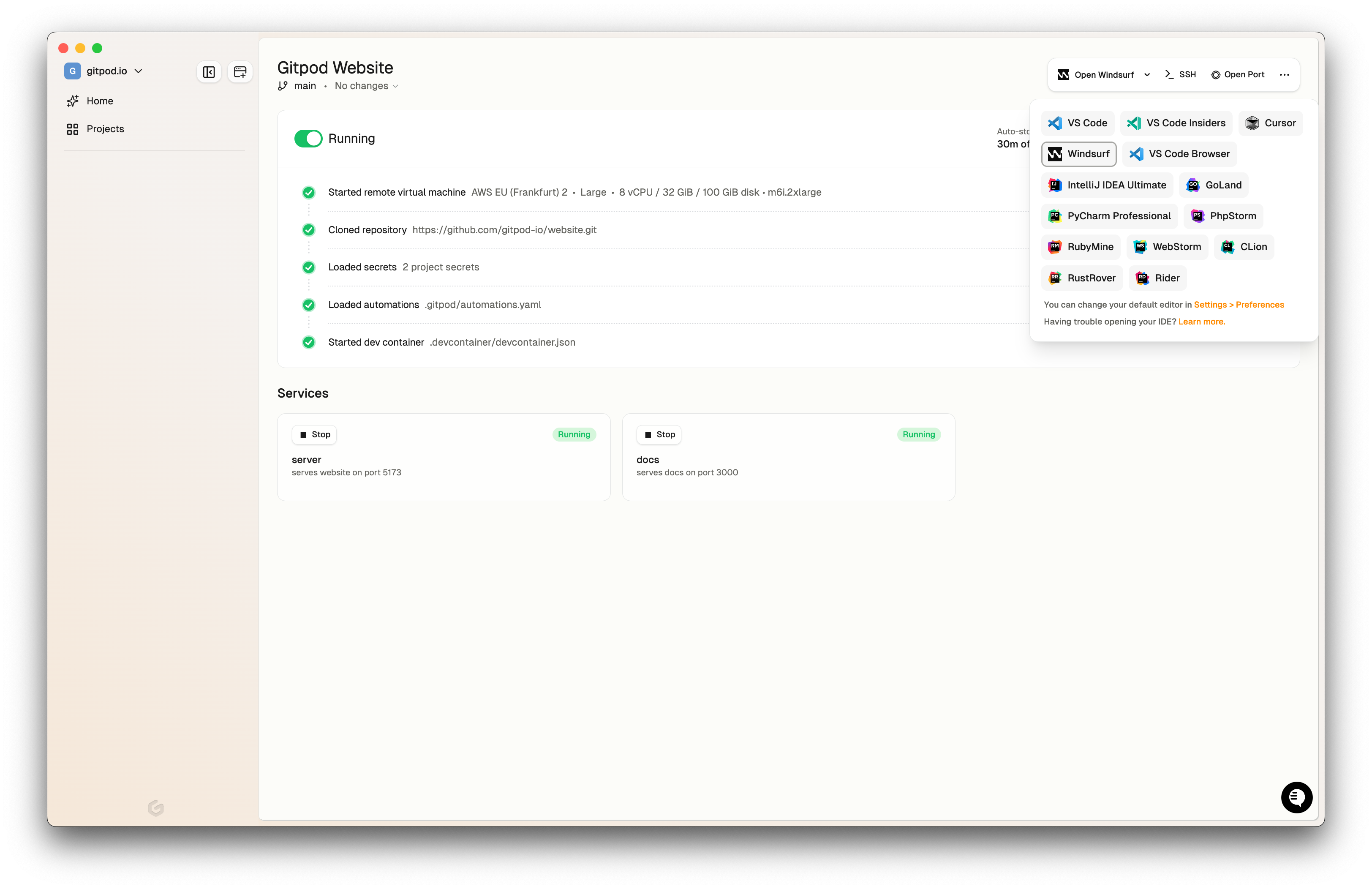
Older updates
Older updates
Older updates
May 2025
Faster development environment start times for AWS with Dev Container build caching
Development environment starts are now faster for organizations using AWS Runners with the addition of a new Dev Container build cache Runner setting that uses Amazon ECR.With this setting enabled you get:- Faster startup times from minutes to seconds for environments with identical Dev Container configurations
- Reclaimed developer time: Convert 5 minute development environment startup delays into 30-second starts
- Automatically optimized start times performance without any configuration changes required
- All subsequent starts using the same project will benefit from significantly faster startup times.
- Images are cached for 30 days before automatically expiring to manage storage costs.
- The cache is restricted to users of the project and can be disabled in runner settings if needed.
- Update your CloudFormation stack to the latest version that supports the cache
- Go to Settings → Runners in your Gitpod organization
- Select your AWS runner and toggle Dev Container image cache to enabled
Analyze your organization’s Gitpod usage with Insights
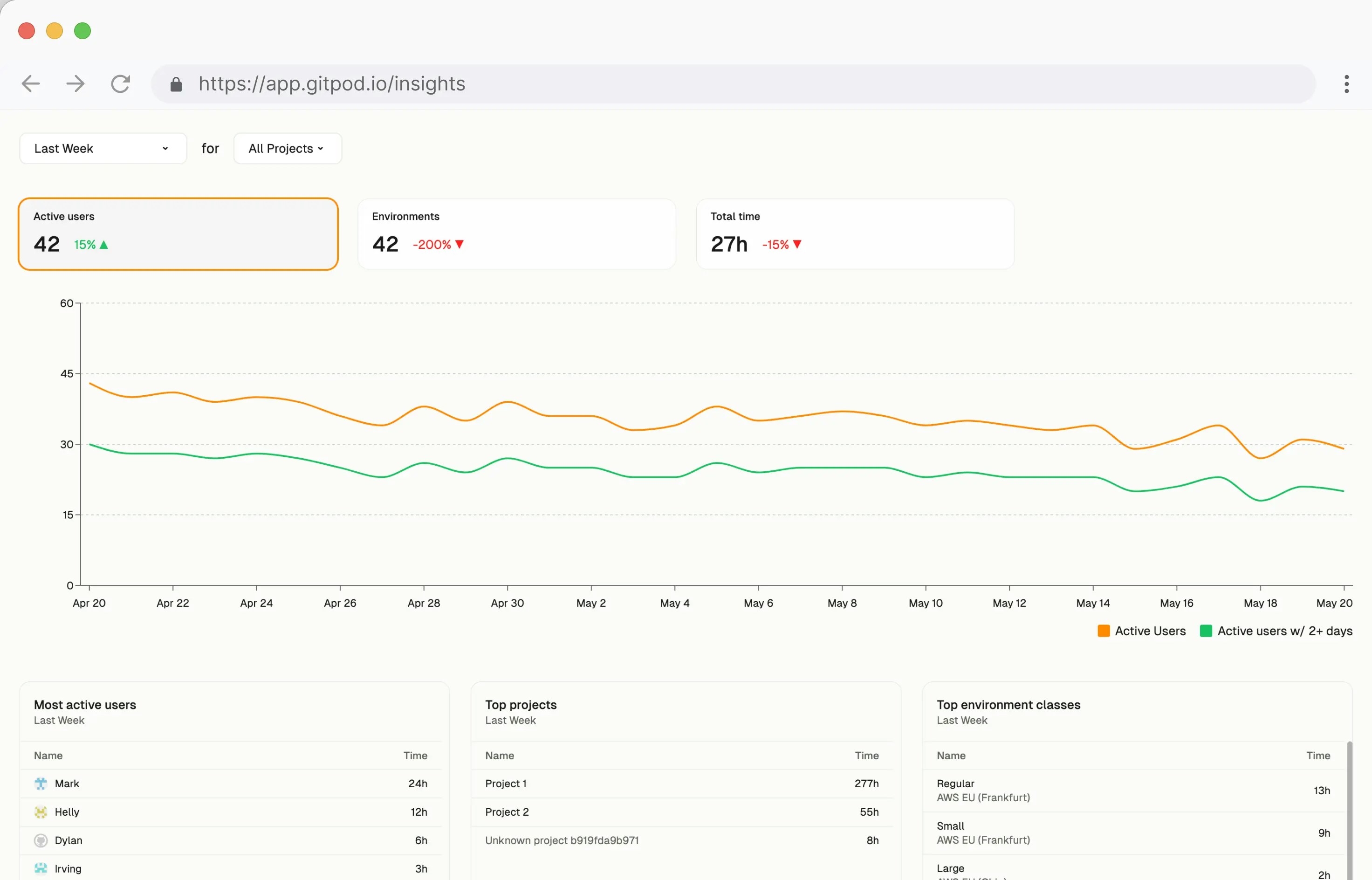
- Analyze environment usage across your entire organization
- Optimize cloud costs by identifying opportunities to right-size resources
- Monitor adoption by tracking active users and environment metrics
- Active Users: Track weekly active users and engagement patterns
- Environment Usage: Monitor total environments and runtime hours
- Resource Distribution: View usage by projects, users, and environment classes
Create development environments from scratch without a Git repository
You can now create development environments from scratch directly from the environment creation modal. This new option allows you to:- Start with a clean slate using your organization’s default environment image
- Start an environment without requiring a git provider configured on a runner
- Begin development immediately without needing to clone an existing repository
- Click the
Create Environmentbutton - Select
Create Environment From Scratch - Choose your preferred environment class
- Click
Createto start your new environment
Organization policies to manage cost, security and developer experience
Organization policies are now available on our Enterprise plan for organizations, giving administrators centralized controls to manage security, developer experience, and resource costs.With Organization policies, you can:- Enhance security - Restrict development environments to only run in the cloud (e.g. not locally) and control which editors developers can use to access your code
- Standardize experience - Create a consistent “golden path” by defining allowed editors and default container images
- Control costs - Set environment timeout limits and maximum environment counts to prevent unexpected resource usage
- Enforce governance - Require environments to be created only from approved projects
- Manage resources - Limit concurrent running environments per user for optimized resource allocation
April 2025
Gitpod now supports VS Code in the Browser
Gitpod now supports VS Code in the browser as well as regular desktop IDEs and editors. Giving developers access to secure development environments without installing any local tools, cloning any source code or managing any dependencies. Development environments that are fully automated and standardized.With Gitpod and VS Code in the Browser, you can:- Drive down your developer onboarding times by eliminating all manual setup for your development teams.
- Empower developers to review code easily by launching new development environments running in their browser tab.
- Drive down incident response times with SREs able to do on-the-go incident response direct from their mobiles.
- For secure enterprises, Gitpod paired with a secure browser (like Island) is a secure and performant alternative to traditional VDI.
Getting started
To get started, simply click the “Open in VS Code in the Browser” button when starting a Gitpod environment. Check our documentation for more details on features and capabilities.Gitpod now supports JetBrains Toolbox App
The JetBrains Toolbox App, a desktop application that helps you manage JetBrains IDEs and projects, now supports remote development in Gitpod environments.This means you can:- Use the familiar Toolbox App interface to manage your IDEs in Gitpod
- Connect to Gitpod environments from your desktop
- Install and update JetBrains IDEs in your remote environment
User Secrets support
We’re excited to announce that Gitpod now supports User secrets, alongside existing Project secrets.With this new feature, you can:- Configure personal secrets for all of your Environments
- Integrate against 3rd party systems which use Personal Access Tokens to authenticate seamlessly, and even use atuin to have persistent terminal history in your Environments.
- Files: Secrets can be mounted as files for complex structures e.g. JSON.
- Environment Variables: Inject secrets as environment variables.
March 2025
AWS ECR private registry support
We’re excited to announce that Gitpod now supports AWS ECR private registries with IAM-based authentication when using AWS EC2 runners.With this new feature, you can:- Securely access private ECR repositories without manually managing credentials
- Simplify authentication workflows using EC2 runner’s IAM role
- Seamlessly work with private container images in your development environment
- You’re using AWS EC2 runners for your environments
- Your ECR registry and EC2 runners are in the same AWS account (or have appropriate cross-account access)
February 2025
Domain Verification for SSO
Domain Verification is now available, allowing organization admins to verify ownership of their email domains through DNS TXT records. This feature strengthens security by confirming domain ownership before enabling SSO functionality. This ensures that only authorized users can access your organization using the specified domain.Learn how to verify your domain from our documentation.Private container registry support
We’re excited to announce that Gitpod now supports Container Registry Secrets, allowing you to securely authenticate with private container registries.With Container Registry Secrets, you can now:- Pull Dev Container images from private registries
- Authenticate with container registries during your development workflow
- Work with private images in your Flex environment without exposing credentials
- Docker Hub
- GitHub Container Registry
- GitLab Container Registry
- Azure Container Registry
Dotfiles Support for Gitpod
Gitpod now supports dotfiles. Dotfiles are a way to customize your developer environment according to your personal needs.Just configure what dotfiles repository to use and Gitpod will clone and install the dotfiles in every environment, ensuring everything is just the way you like it.Head over to the documentation to learn how to get started.December 2024
Introducing Gitpod SSO
We’re excited to announce that Gitpod now supports Single Sign-On (SSO), making it easier than ever to manage access for your team. With SSO, your team can log in using their existing accounts with trusted Identity Providers like Okta, Azure AD, or Google using OpenID Connect (OIDC) integration.This feature simplifies authentication by eliminating the need for separate credentials, enhances security by centralizing user management, and streamlines access across your organization. As an admin, you can easily set up SSO in your organization’s settings using your IdP credentials and manage access with just a few clicks.Learn how to set up SSO in our documentation.Introducing Gitpod secrets & environment variables
Gitpod now supports secrets and environment variables. Securely store and inject sensitive data such as API keys and access credentials into your development environment. Secrets are encrypted using AES256-GCM and stored securely. Only environments launched from an associated project can access it’s secrets.Highlights:- Environment Variables: Inject secrets as environment variables.
- Files: Secrets can be mounted as files for complex structures e.g. JSON.