Prerequisites
- Organization administrator permissions
- An existing project with at least one environment class configured
- AWS or GCP Enterprise runner or Ona Cloud
Enable prebuilds
1. Navigate to project settings
- Go to your organization dashboard at https://app.ona.com
- Select your project from the projects list
- Click on the project to open its settings
2. Configure prebuild settings
In the project settings, you’ll find the prebuild configuration section where you can:- Enable prebuilds for the project
- Select environment classes for which prebuilds should be created
- Configure the schedule for automatic prebuild creation
- Configure the executor to run prebuilds as yourself or a service account
- Set timeout for prebuild execution (only configurable through the CLI right now)
- The daily schedule stops running
- New environments will no longer use existing prebuild snapshots
- Existing prebuild snapshots remain until they expire (7 days)
3. Select environment classes
Choose which environment classes should have prebuilds created:- Check the boxes next to the environment classes you want to prebuild
- Prebuilds will be created for each selected class on the configured schedule
- Consider your team’s usage patterns when selecting classes
4. Configure the executor
Choose which identity runs your prebuilds:- User (default): Prebuilds run as the user who enabled prebuilds for the project
- Service account: Prebuilds run as a service account, using the service account’s SCM credentials
- Ensures prebuilds continue working regardless of individual user availability
- Provides consistent permissions independent of user role changes
- Clearly attributes prebuild activity to a dedicated account
- The service account must have Git authentication configured on all runners where prebuilds will run
- The service account’s Personal Access Token must have access to the project’s repository
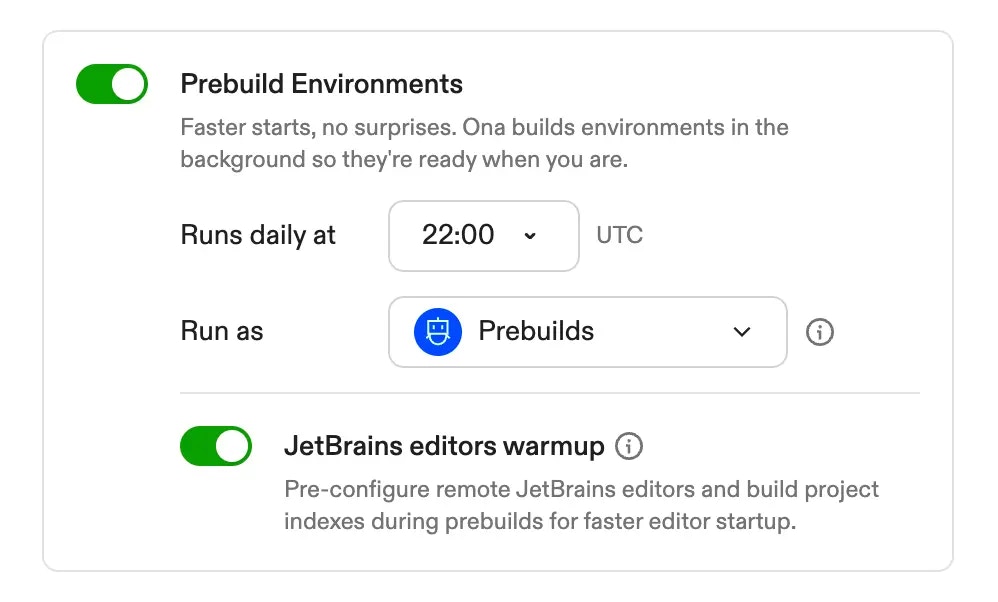
5. Configure the schedule
Set up when prebuilds should run automatically:- Daily schedule: Choose the hour (UTC) when prebuilds should trigger
- Recommended timing: Schedule prebuilds during off-hours (e.g., 2 AM UTC) so fresh prebuilds are ready when your team starts work
6. Set timeout (via CLI)
Configure how long prebuilds can run before timing out using the CLI:7. Configure JetBrains warmup (optional)
If your team uses JetBrains editors, enable JetBrains warmup to pre-install the editor backend and build project indexes during prebuilds:- In the prebuild configuration section, enable JetBrains warmup
- Configure recommended editors to specify which JetBrains editors to warm up
- Eliminates editor backend download time when users open the editor
- Prebuilt indexes mean instant code navigation and analysis
- Consistent experience across all team members
Configure your Dev Container for prebuilds
To get the most out of prebuilds, structure your Dev Container configuration appropriately:Commands that run during prebuilds
Place time-consuming setup tasks in these lifecycle hooks:Commands that run after prebuilds
Place user-specific or session-specific commands here:Configure tasks and services for prebuilds
You can also configure automation tasks to run during prebuilds by adding theprebuild trigger:
prebuild trigger will execute during prebuild creation, alongside your Dev Container lifecycle commands.
Note: Organization and project secrets are available to automation tasks during prebuilds, but user secrets are not. Ensure any credentials needed for prebuild tasks are configured at the organization or project level.
Manually trigger a prebuild
In addition to scheduled prebuilds, you can manually trigger prebuilds:Via web UI
- Navigate to your project settings
- Click the Prebuild button in the top right corner
- Testing prebuild configuration changes
- Creating a fresh prebuild after significant code changes
- Preparing prebuilds before scheduled time
Via CLI
You can also trigger prebuilds for specific environment classes using the CLI:Verify your setup
After enabling prebuilds, test your configuration to ensure everything works correctly:- Trigger a manual prebuild to verify it completes successfully
- Check the prebuild logs for any errors or warnings
- Create a new environment and confirm it starts from the prebuild
- Verify the schedule is set correctly for your timezone
Best practices
Optimizing for speed and cost
Only install dependencies necessary for development. Schedule prebuilds during off-hours (e.g., 2 AM UTC) so fresh prebuilds are ready when your team starts work. Start by enabling prebuilds for one or two commonly used environment classes, then expand based on usage patterns and cost considerations.Structuring your commands
Place stable, time-consuming operations in prebuild commands: dependency installation, database seeding, and asset downloads. ReservepostCreateCommand for dynamic operations like starting dev servers or user-specific setup. Ensure all commands are idempotent so they can run multiple times safely.
Managing secrets
Use organization secrets for shared credentials needed during builds, and project secrets for project-specific credentials. Remember that user secrets aren’t available during prebuilds, so ensure any required credentials are configured at the organization or project level.Troubleshooting
Cannot trigger prebuild: Ensure prebuilds are enabled for the project in project settings. You’ll see an error if you try to trigger a prebuild on a project that doesn’t have prebuilds enabled. Prebuild fails to complete: Check logs for error messages, verify secrets are configured correctly, and ensure commands don’t require user interaction. If builds consistently timeout, increase the timeout using the CLI. Environment doesn’t use prebuild: Verify a successful prebuild exists for the environment class, check it’s less than 7 days old, and ensure the environment class matches exactly. Prebuild succeeds but environment has issues: Some commands may need to run per-environment rather than in the prebuild. Move user-specific or session-specific commands topostCreateCommand, and verify file permissions are correct after the snapshot.
For more detailed troubleshooting guidance, see Managing Prebuilds.