Requires Core or Enterprise plan.
How it works
- User provides input to Ona Agent
- Agent decides to execute a command
- System checks command against deny list
- Command is executed (if allowed) or blocked with error message
Pattern matching
| Pattern | Effect |
|---|---|
shutdown | Blocks exactly “shutdown” |
shutdown* | Blocks “shutdown”, “shutdown -h”, “shutdown now” |
rm * | Blocks all rm commands with arguments |
Slash commands (
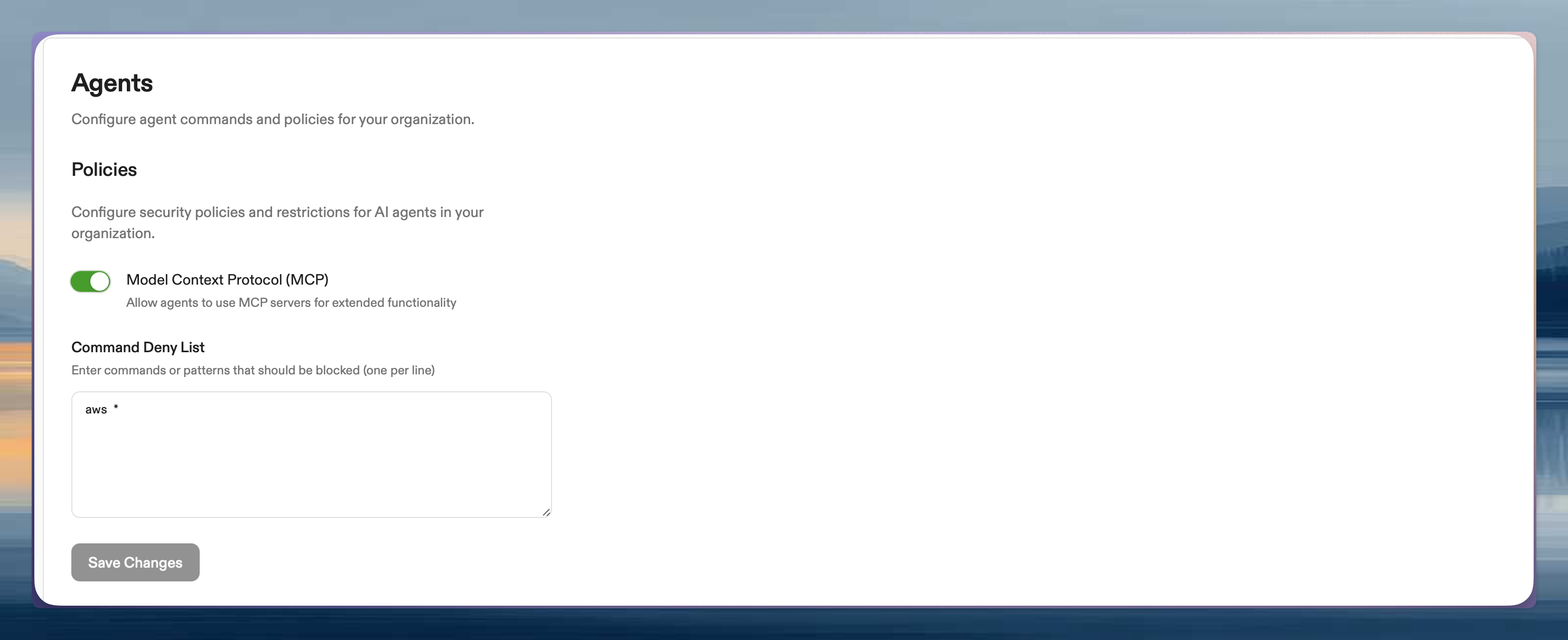
/clear, /support-bundle) are NOT blocked by deny lists—they’re converted to prompts before reaching the agent. Bash commands (prefixed with !) are subject to deny list filtering.Configuration
Go to Settings → Agents. Only administrators can access.- Locate the Policies section
- Add patterns to Command Deny List (one per line)
- Save changes
Example patterns
Effect on users
When blocked, users see:- Manual commands unaffected: Users can still run commands directly in terminal
- Agent only: Only Ona Agent execution is restricted
- No retries: Agent is instructed not to retry blocked commands
Security considerations
Protects against:- Accidental destructive commands
- Malicious prompt injection
- Compliance violations
- Resource abuse
- Direct user commands in terminal
- Application-level actions
- Slash commands (cannot be blocked via deny lists)
Best practices
- Start with broad patterns (
aws *instead of listing variants) - Test in a non-production environment first
- Document why patterns were added
- Review and update periodically
Testing
- Create a new environment
- Ask Ona Agent to run a blocked command
- Verify the error message appears