What you’ll do
Add a secret that your environments and agents can use. We’ll use a Linear API key as an example, but the process is the same for any credential.Choose a scope
Secrets can be configured at three levels:| Scope | Best for |
|---|---|
| User | Personal API keys (Linear, GitHub tokens). Only available in your environments. |
| Project | Shared credentials for a specific repository. Available to all project members. |
| Organization | Company-wide credentials. Available across all projects. |
Add a user secret
- Go to Settings > My Account > Secrets
- Click New Secret
- Configure:
- Type: Environment Variable
- Name:
LINEAR_API_KEY - Value: Your Linear API key (from Linear Settings > API)
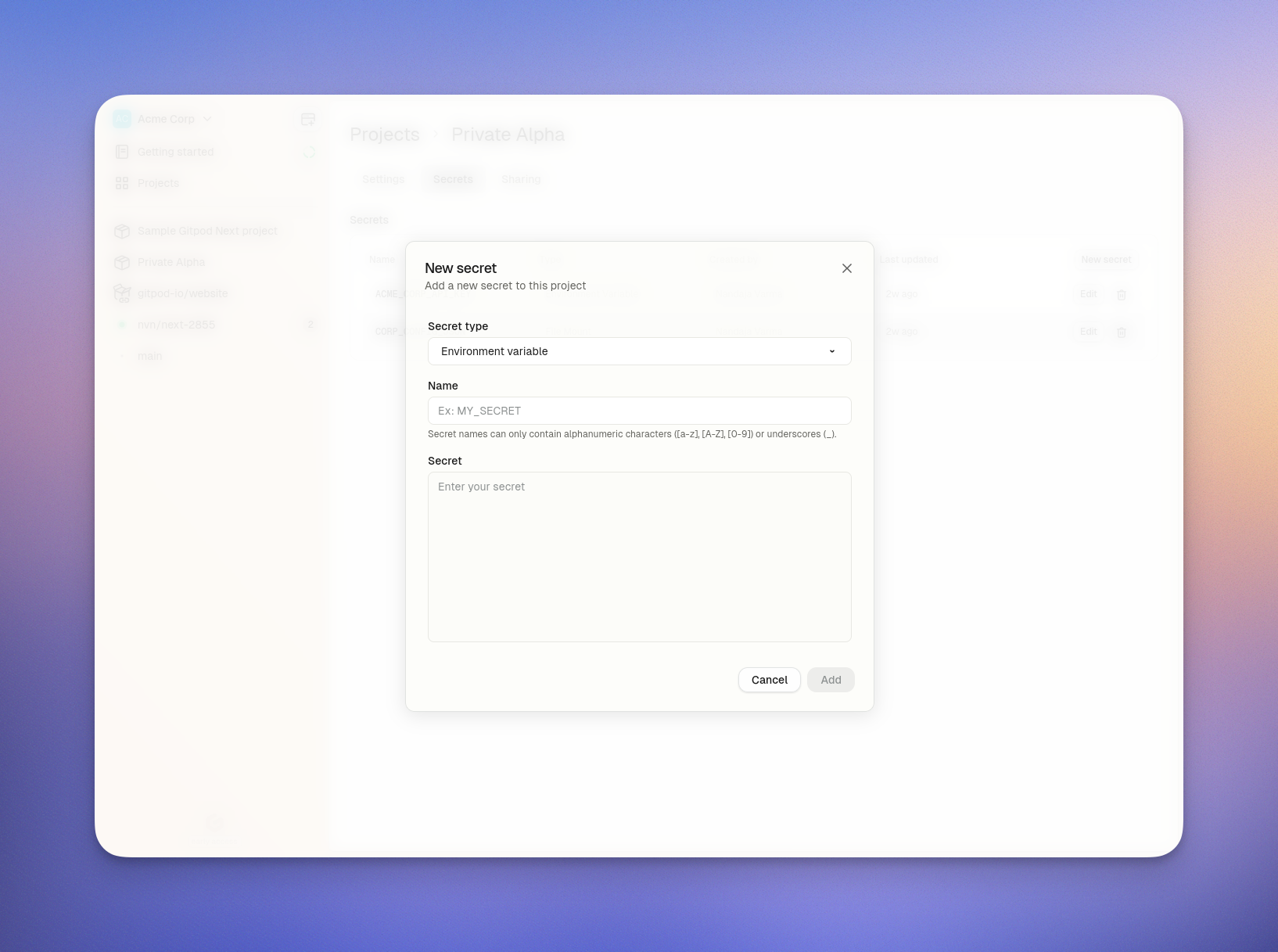
- Click Create
Security tradeoff: Environment variables can leak through process listings and logs. File secrets are more secure, but many tools (including MCP servers) expect credentials as environment variables. For API keys that can be rotated, this tradeoff is often acceptable. For passwords and private keys, prefer file secrets.
Verify it works
Start an environment and check the secret is injected:Common secrets for agents
| Secret | What it enables |
|---|---|
LINEAR_API_KEY | Issue creation and management via Linear MCP |
GITHUB_TOKEN | Enhanced GitHub access via GitHub MCP |
OPENAI_API_KEY | Custom LLM providers |
AWS_* credentials | Cloud resource access |
Secret precedence
If the same secret name exists at multiple levels, user secrets override project secrets, which override organization secrets. This lets you use personal credentials while teams share defaults.Next steps
- Configure Linear to use your API key
- Learn about MCP servers that use secrets
- Secrets reference for all secret types