Cost consideration: VPC endpoints incur additional AWS charges (~$7.20/month per endpoint per AZ plus data processing fees). See AWS PrivateLink pricing for details.
Prerequisites
Before creating VPC endpoints, ensure:- Your VPC has both DNS hostnames and DNS resolution enabled
- You have the VPC ID, subnet IDs, and security group IDs ready
- You’re creating endpoints in the same region as your runner deployment
Required VPC Endpoints
Replace<region> with your AWS region when creating these endpoints.
Interface Endpoints
| Service | VPC Endpoint Service Name |
|---|---|
| EC2 | com.amazonaws.<region>.ec2 |
| ECR API | com.amazonaws.<region>.ecr.api |
| ECR Docker | com.amazonaws.<region>.ecr.dkr |
| SSM | com.amazonaws.<region>.ssm |
| STS | com.amazonaws.<region>.sts |
| CloudFormation | com.amazonaws.<region>.cloudformation |
| Secrets Manager | com.amazonaws.<region>.secretsmanager |
| ECS | com.amazonaws.<region>.ecs |
| ECS Agent | com.amazonaws.<region>.ecs-agent |
| ECS Telemetry | com.amazonaws.<region>.ecs-telemetry |
| SSM Messages | com.amazonaws.<region>.ssmmessages |
| EC2 Messages | com.amazonaws.<region>.ec2messages |
| CloudWatch Logs | com.amazonaws.<region>.logs |
| Elastic Load Balancing | com.amazonaws.<region>.elasticloadbalancing |
| ACM | com.amazonaws.<region>.acm |
Gateway Endpoints
| Service | VPC Endpoint Service Name |
|---|---|
| S3 | com.amazonaws.<region>.s3 |
| DynamoDB | com.amazonaws.<region>.dynamodb |
Gateway endpoints (S3, DynamoDB) are configured differently than interface endpoints. See the AWS documentation on gateway endpoints for details.
Creating VPC Endpoints
Using AWS CLI
Using AWS PowerShell
Using AWS Management Console
-
Navigate to VPC Console
- Open the AWS VPC Console
- Select “Endpoints” from the left navigation
-
Create Endpoint
- Click “Create endpoint”
- Name tag (optional): Enter a descriptive name like
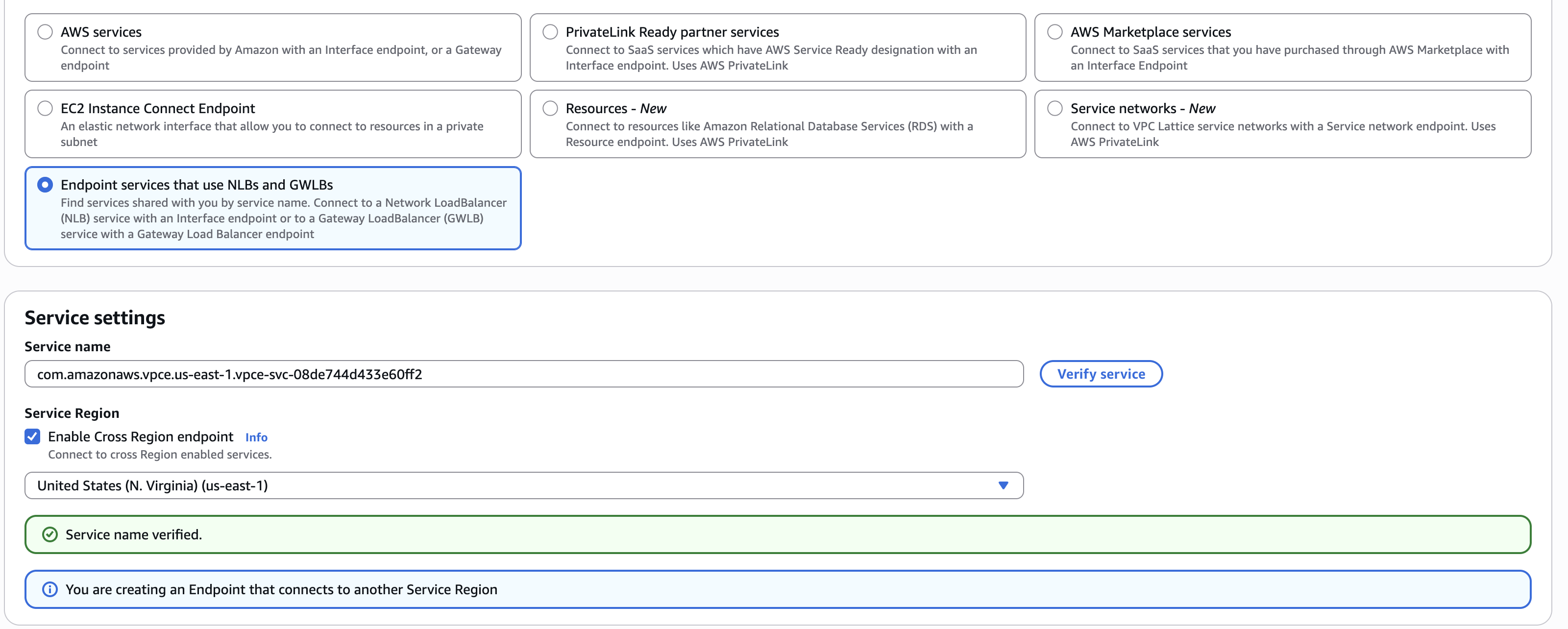
ona-management-plane - Service type: Select “Endpoint services that use NLBs and GWLBs”
-
Service Settings
- Service name: Enter
com.amazonaws.vpce.us-east-1.vpce-svc-08de744d433e60ff2 - Enable Cross Region endpoint: Check this box to connect across regions (Note: For us-east-1 region, leave this unchecked)
- Region: Select us-east-1 as the region
- Click “Verify service” to confirm the service is available
- Service name: Enter
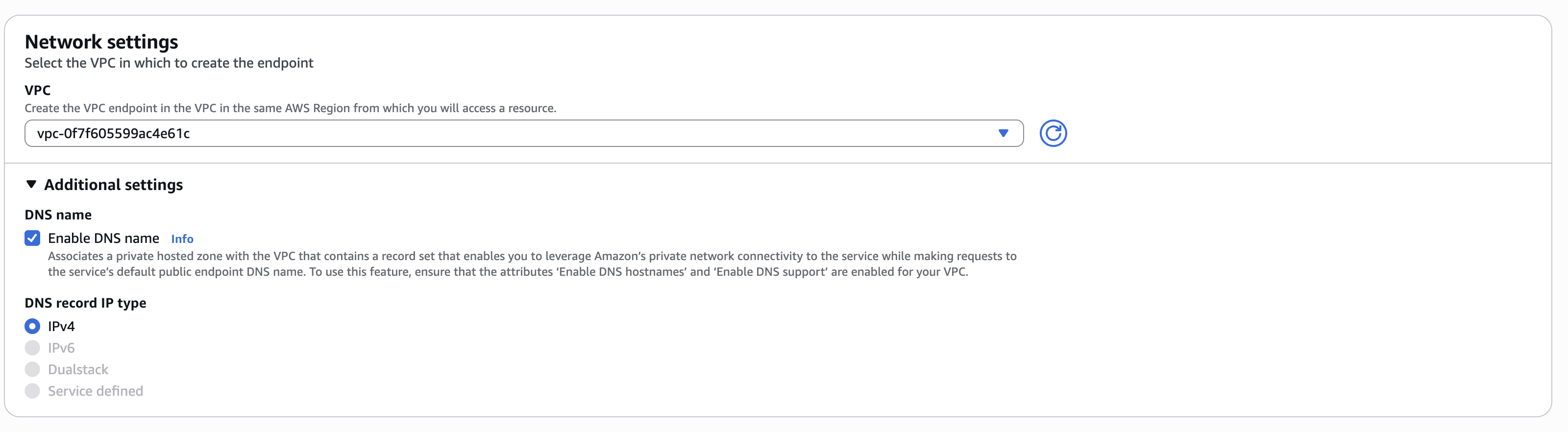
- Network Settings
- VPC: Select the same VPC where your runner is deployed
- Enable DNS name: Check this box to enable private DNS names (this allows
app.gitpod.ioto resolve to the endpoint) - Subnets: Choose private subnets in available AZs (can be the same subnets as your EC2 runner instances)
- Security groups: Select or create a security group that allows HTTPS traffic (port 443, inbound). Include the runner security group and the security group for environment access (you can find these in the Output section of the Runner Cloud Formation template).
- Create and Verify
- Click “Create endpoint”
- Wait for the endpoint status to become “Available”
Key Configuration Settings
When creating interface endpoints:- Enable private DNS names: This allows AWS service hostnames to resolve to your VPC endpoint’s private IP addresses
- Subnets: Select subnets in multiple availability zones for high availability
- Security groups: Configure to allow HTTPS (443) traffic from your runner subnets
us-east-1 region specific: When creating VPC endpoints in the us-east-1 region, disable cross-region support. This is due to availability zone mapping differences between AWS accounts that can prevent endpoint creation. The endpoint only needs to exist in one AZ within your VPC - clients in other AZs can still reach it via DNS.
Security Group Configuration
Your VPC endpoint security group needs these rules: Inbound Rules:- Type: HTTPS (443)
- Source: Your runner subnets CIDR or the security group attached to your runner instances
- Description: Allow runner access to AWS services
- Type: All traffic
- Destination: 0.0.0.0/0 (or keep the default outbound rule)
Verification
After creating the VPC endpoints:- Check endpoint status in the VPC console - all endpoints should show as “Available”
- Verify private DNS resolution from an instance in your VPC:
This should resolve to private IP addresses within your VPC CIDR range
- Test connectivity by deploying or accessing your runner
Troubleshooting
If you encounter issues with VPC endpoints:- DNS resolution fails: Verify DNS hostnames and DNS resolution are enabled on your VPC
- Connection timeouts: Check security group rules allow HTTPS (443) from runner subnets
- Endpoint creation fails in us-east-1: Disable cross-region support when creating the endpoint
- Service unavailable: Ensure the endpoint is in “Available” state and private DNS is enabled